GraphQL Inspection
The Fastly Next-Gen WAF provides the ability to parse GraphQL requests, enabling visibility and protection against GraphQL attacks.
On this page
Visibility and protection for your GraphQL APIs
The evolution of API development has played a key role in the explosive growth of dynamic applications. Organizations are seeking more efficient ways to speed up release cycles, and this velocity is changing the CI/CD pipeline, from how releases are organized (from waterfall to agile development, for example) all the way down to the architecture level.
While REST and SOAP have played a major role in how APIs are written, GraphQL is quickly becoming a developer favorite for its efficiency, speed, and specificity.
The Fastly Next-Gen WAF (powered by Signal Sciences) provides advanced protection for your applications, APIs, and microservices, wherever they live, from a single unified solution. With the addition of GraphQL Inspection, we have expanded our coverage over your APIs, no matter what architecture or specification your developers use.
While REST has set the standard for API development over the past two decades, organizations are quickly adopting GraphQL as a more efficient way to make calls that power their applications.
Setting a new standard for API protection
The strength of GraphQL over REST is that it allows the caller to request the exact information they need without returning any extraneous data. And this is done with a single call instead of making multiple roundtrips to the backend which decreases overall server strain.
The increased adoption of the open-source query language GraphQL demonstrates how developers are moving away from REST-based APIs to a specification that is faster and more efficient. While this provides a better experience for both developers and the end-users, GraphQL is still subject to OWASP API Top 10 attacks, as well as GraphQL-specific exploits.
The Fastly Next-Gen WAF offers coverage that blocks OWASP-style injection attacks, denial of service attacks, and other vulnerabilities that can target GraphQL APIs. GraphQL Inspection gives your teams the ability to adopt newer technologies without taking on additional application security risk. With almost 90% of customers in full blocking mode, we provide comprehensive API protection that doesn’t break your application or block legitimate requests.
Key benefits
Increased API attack visibility and coverage
As your organization increases its application footprint, the Fastly Next-Gen WAF provides scalable and comprehensive protection across all of your Layer 7 assets with full feature parity. Teams can apply their existing WAF rules to GraphQL requests and block attacks, or create custom rules to specifically handle GraphQL traffic.
Protection where your developers are
Help your developers to deploy applications using the tools they want, without slowing down release cycles. GraphQL Inspection allows organizations to write APIs safely while giving development teams the freedom and flexibility to work within the languages that fit into their workflows.
Operational efficiency
GraphQL Inspection enables you to reap the benefits of GraphQL’s efficiency improvements without putting your applications at risk.
Blocking GraphQL attacks
GraphQL Inspection for the Fastly Next-Gen WAF offers several ways for you to take advantage of our patented approach to security:
Automation
As a part of our out-of-the-box solution, GraphQL Inspection will parse GraphQL requests and inspect the contents of the request within context. If an OWASP-style attack is present, we will block it automatically without any additional setup and configuration required.
Custom Signals
Fastly provides GraphQL-specific signals in the console for customized protection based on user configuration. With these signals, you can define rules to route requests when certain thresholds or events happen. Some of these signals are included below.
A signal is a descriptive tag about a request. It makes certain characteristics of the request visible and apparent – this includes what types of attack payloads a request contains or whether the request was blocked.
Templated Rules
Includes a templated rule around requests for a GraphQL IDE. GraphQL attacks are now visible via the console.
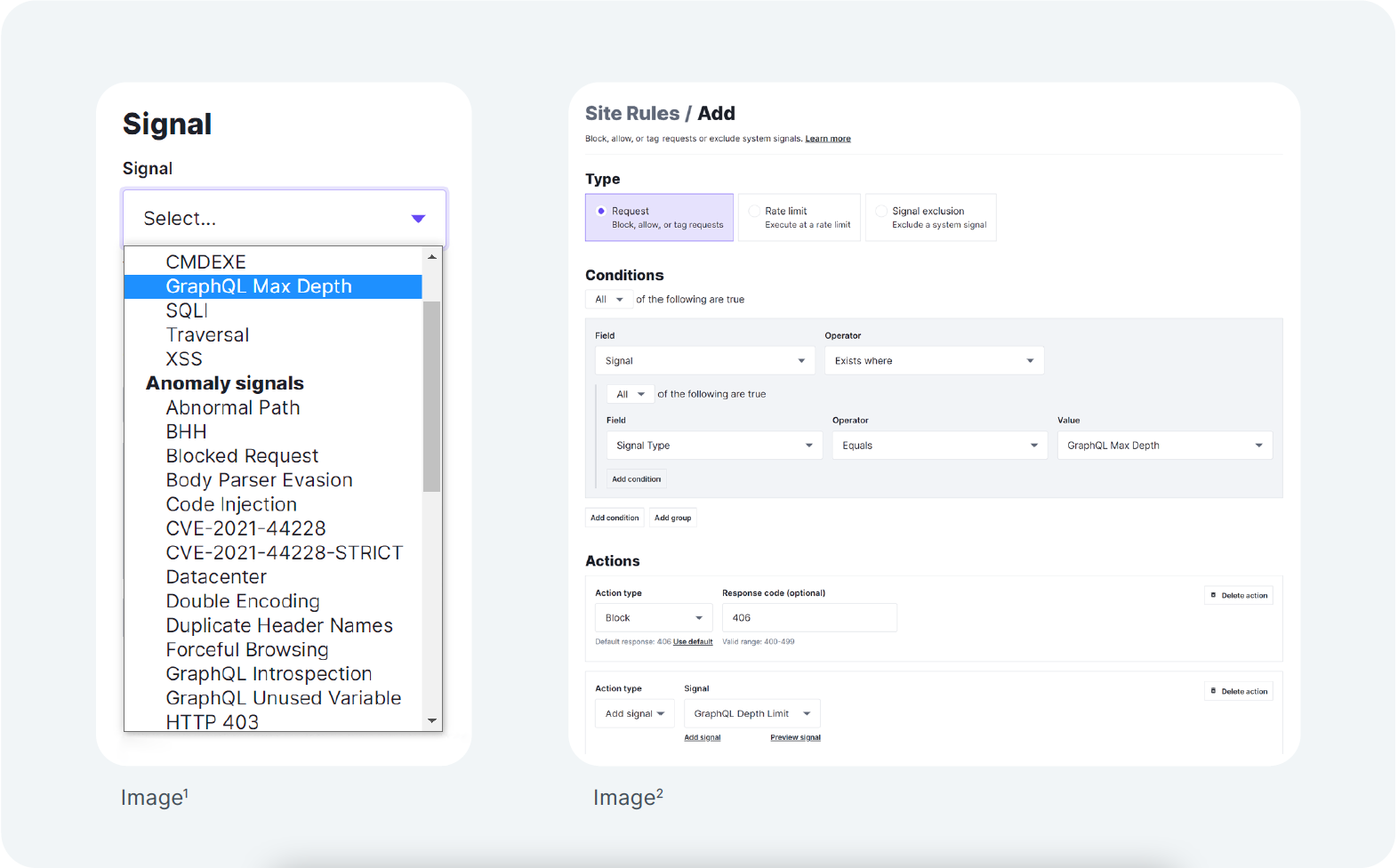
Common GraphQL vulnerabilities and Next-Gen WAF anomaly signal examples
OWASP API Security Top 10
Injection Attacks
SQL Injection
Command Injection
Server-side Request Forgery
Denial of Service
Broken Access Controls
GraphQL-specific
Max Depth - complex queries that crash servers
Introspection - public data exposure through queries
Unused variables - sign of an attack within request
Ressources connexes
Get ahead of security considerations for your applications and APIs using GraphQL.
Fastly is a Cloud WAAP Challenger. Compare vendors in this report.
Fastly is the only vendor to be named a Customers’ Choice for five consecutive years.
Learn defaults and controls for a safer and more successful GraphQL implementation.