The holiday shopping season generates a TON of revenue for online retailers. In 2022 Black Friday alone generated over $9 billion according to Adobe’s annual Holiday Shopping Report. It also generates a ton of spiky traffic to drive that level of sales, which means that speed and reliability are critical, and site reliability engineers (SREs) are under the gun.
Downtime during the shopping season can cost a company much more than on other days of the year – even making companies miss important quarterly or annual targets, so there are two goals:
Keep the site available, fast, and running well
Don’t ruin your SRE’s holiday weekends by making them put out fires and block attacks when you could have prepared in advance
As a Security Technical Account Manager (STAM), my job is to help support our customers with technical training, health checks, configuration, and more. I want to share eight recommendations to optimize your Fastly Next-Gen WAF (NGWAF) ahead of big increases in holiday shopping traffic for a smoother, more profitable Black Friday weekend.
1. Ensure Templated Rules are enabled and configured correctly on key pages
Templated Rules are an incredibly easy way to turn on powerful protections, targeting the most common attacks our customers see. Our team also publishes Templated Rules for high-impact vulnerabilities, like CVEs and Zero Day attacks - many of which we’ve released in less than one hour.
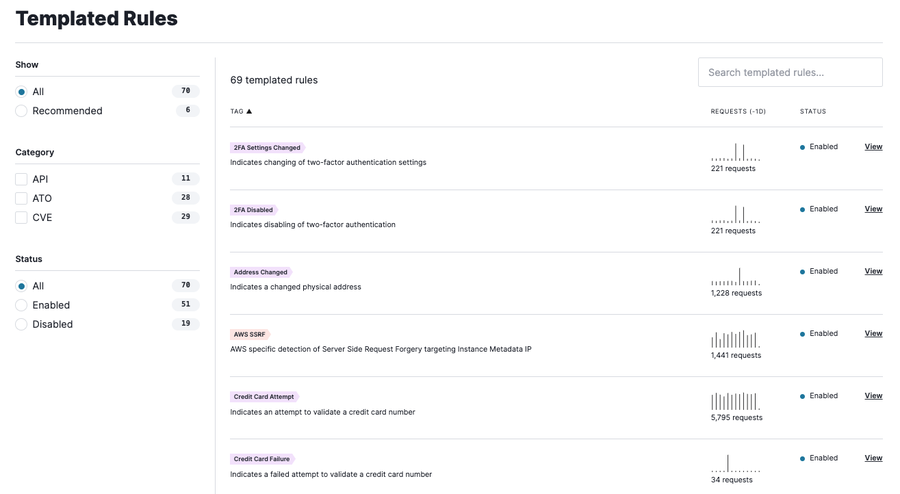
Enabling templated rules on your apps and APIs prevent attacks like malicious account takeovers, credit card attempts, and gift card fraud from impacting your Black Friday weekend. To protect your key login and checkout pages, make sure to enable our Templated Rules for the following:
Account Takeover (ATO)-specific Templated Rules to track logins, registrations, gift cards, email and password changes.
API-specific Templated Rules specific to GraphQL, Resource and UserEnumeration attacks, and Unexpected API Clients, to name a few.
CVE Templated Rules (we have more than 29 at present) that correlates to your application use cases.
2. Deploy our Gold Standard Attack Signal rule
As a STAM, I work with my customers to onboard and guide them through enabling our NGWAF and its custom signal and rule features. The first rule I implement for customers is our “gold standard”, which automatically blocks attacks from a number of our out-of-the-box signals.
These attack signals add depth to your blocking techniques and significantly reduce the rate of false positives. For example, the signal SigSci IP indicates verified customer attacks that come through our Network Learning Exchange.
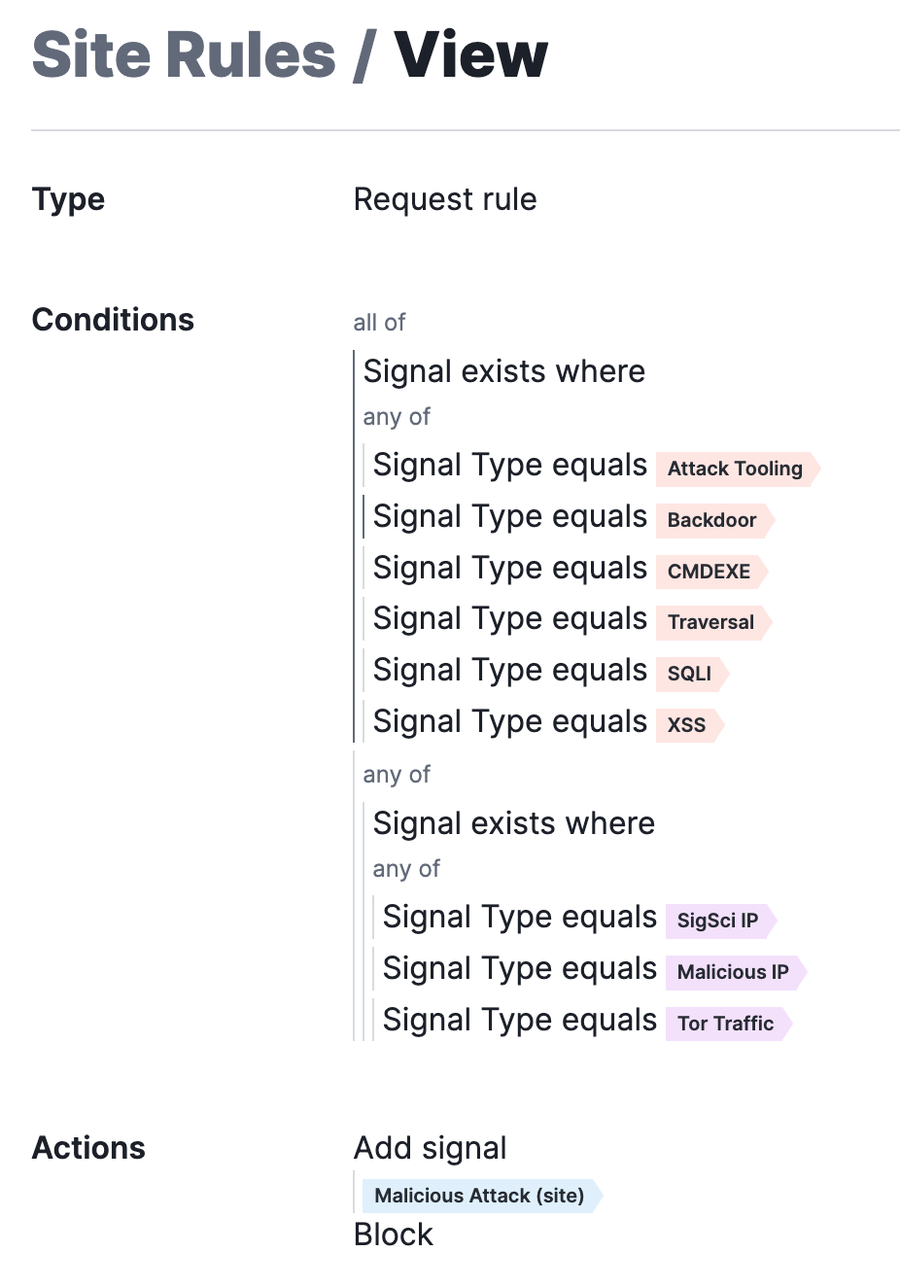
Our intuitive rule builder makes it easy to implement and deploy this rule as part of your Black Friday preparations. To create this rule, go to the NGWAF console and
Select your site
Navigate to the rules menu, select “Site Rules” and click the “Add Site Rule” button
Create a request rule with the following conditions:
Signal exists where
Signal Type equals
Attack ToolingBackdoorCMDEXETraversalSQLiXSS
Signals exists where
Signal Type Equals
SigSci IPMalicious IPTor Traffic
Action Type
Block
Add Signal
Malicious Attack (Site)
3. Reduce attack signal thresholds
There’s a difference between detection and enforcement. With most WAFs, they are considered the same, and they block everything that matches a rule. The Fastly NGWAF is unique in offering thresholding as an additional layer of false positive tolerance. This is because when we see real attacks, it’s usually on the order of hundreds or thousands of requests.
To prepare for Black Friday weekend, it’s important to adjust your thresholds to scale with your expected traffic spikes and prevent “low and slow” attacks that attempt to evade detection.
By default, attack signals are set to 50 requests in 1 minute. I recommend reviewing existing default attack signal thresholds and reducing these based on the percentage of observed sources that are close, but not passing, your existing threshold.
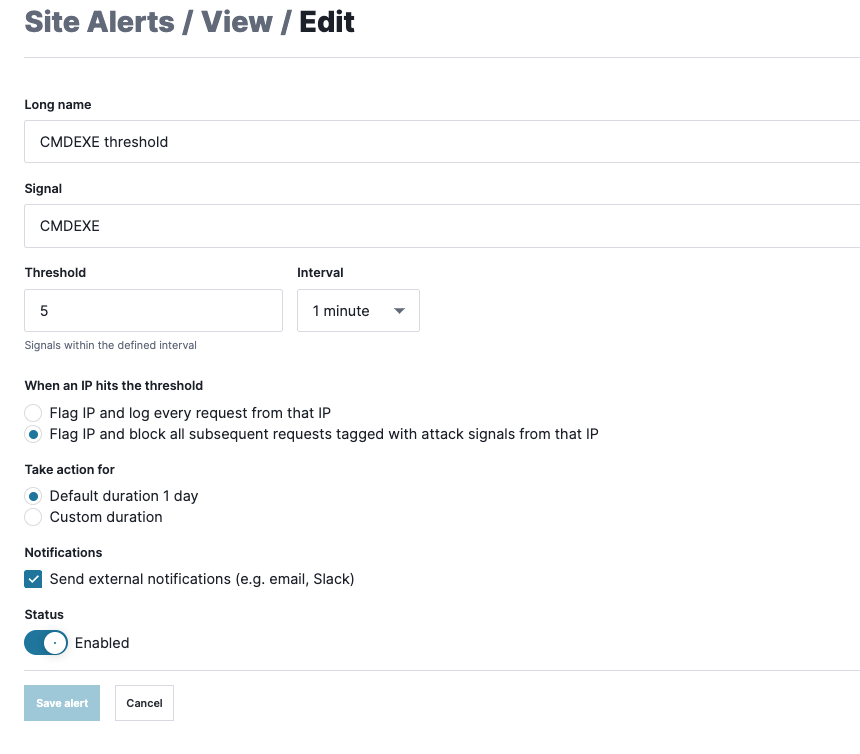
To adjust attack thresholds, navigate to the Rules menu and select “Site Alerts”. Select the attack and click “Edit Site Alert”
To see IPs that are approaching thresholds or triggering actions, navigate to the Monitor menu, select “Observed Sources” then “Suspicious IPs”
4. Add JA3 client-side fingerprinting
One responsibility I have as a STAM is to help my customers take advantage of the security features available across our entire product line. For customers using both Fastly Delivery and NGWAF, I recommend adding JA3 client-side fingerprinting as an additional mitigation strategy for stopping attacks during Black Friday weekend.
JA3 TLS fingerprinting is an open source technique to attach unique identifiers to TLS clients. For Fastly security customers, this means we can detect and block malicious requests, such as bot attacks, even if an attacker switches IPs.
To enable JA3, navigate to the Fastly Delivery console and add this VCL Line
set req.http.X-Tls-Ja3 = tls.client.ja3_md5;Since JA3 is best used when working with other conditions, I recommend adding the following signal feeds to it:
Malicious IPSigSci IPTOR TrafficSuspected Bad Bot
If you have our NGWAF deployed at the edge or are part of Fastly Security Labs, JA3 will already be enabled for you. If you’re not comfortable working in VCL or want to learn more about JA3 fingerprinting, reach out to your STAM or support team for assistance.
5. Deploy Bot Signals best practices
One of the top concerns for my customers on Black Friday weekend are bad bots - malicious, automated attacks that impersonate real customer behavior to commit fraud or disrupt applications and APIs. These attacks can range from low-and-slow requests to volumetric surges of malicious traffic. But unfortunately, many bot mitigation techniques can also block legitimate users from navigating the site, which can be devastating for user experience and retail sales.
To block bad bots, I recommend creating a best practice rule with the following conditions. This includes SigSci IP, which only blocks bad requests from bad IP for further false positive reduction:

Select your site
Navigate to the rules menu, select “Site Rules” and click the “Add Site Rule” button
Create a request rule with the following conditions:
Signal exists where
Signal Type equals
Suspected Bad Bots
Signals exists where
Signal Type Equals
SigSci IPMalicious IPTor Traffic
Action Type
Block
6. Audit integrations and notifications
When preparing for a high-impact event, the last thing I want you to worry about is missing important notifications and disrupting your usual workflows. Every team I work with has preferred tools, integrations, and ways to be notified when something goes wrong. The Fastly NGWAF has a number of best-in-class integrations to help security and SRE teams maintain smooth operations during high-traffic events.
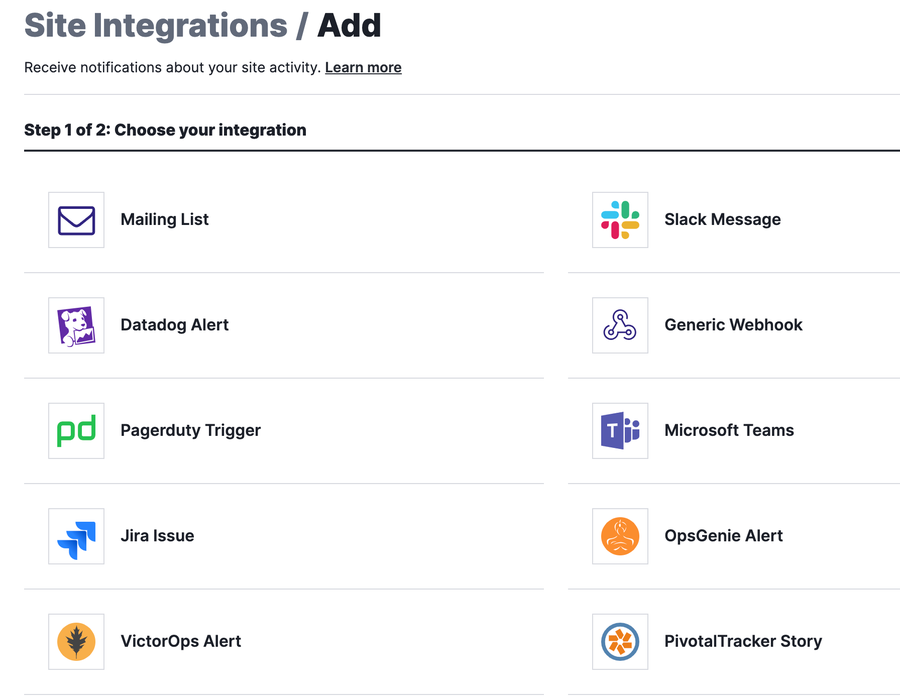
To minimize disruptions and maximize visibility, I recommend you audit your site integrations and notifications, then adjusting them according to your anticipated Black Friday needs. We support email, Slack, generic webhooks, and others to ensure you are notified for security-specific activity before it impacts site performance or user experience.
After setting up your integration, you can ask the NGWAF to notify you about specific activity. If you want to be thorough, you can select “All Activity”. But our standard recommendation is:
IP flag manually expired
Agent alert
Templated rule updated
Redaction updated
Rule updated
7. Request a site survey from your Security Technical Account Manager (STAM)
So far I’ve walked through some of the easy ways that your team can utilize the NGWAF’s features to prepare for Black Friday. But for many teams, a dedicated expert can accelerate your efforts and act as an additional security resource by conducting a site survey.
With a site survey, a STAM can provide information on your sites to help drive team strategy and focus. It’s like hitting an “easy button” to save you and your team on resources that can be diverted to higher-impact activities. A site survey can include:
Review of your corp/site rules
Review of your site thresholds
Review of any endpoints currently not being protected
Analyze for anomalous requests
If you do not have a STAM, reach out to your account team to request one.
8. Verify configuration backups
Great teams know that it’s not just about preventing disaster, but knowing how quickly they can recover from one. When preparing for a Black Friday worst-case scenario, like a catastrophic site crash, I work with my customers to make sure that they have configuration backups set up and ready to go.
If you use a configuration backup solution like Terraform, I highly recommend that you create a backup of your current Fastly NGWAF corp/site(s) configuration. In general, I recommend this practice before any event or before making any major changes to the site. But in the case of Black Friday weekend, verifying your configuration backups in advance will help ensure that if something breaks, you can get the application or API back online with all of your settings in place. This reduces the attack surface during a vulnerable period and allows security teams to spend less time on re-configuring their settings, and more time on resolving outstanding issues.
Looking beyond Black Friday Weekend
We hope these tips have highlighted potential opportunities for the Fastly NGWAF to help better protect your apps and APIs throughout the holiday shopping season. If you’re already a NGWAF customer, these recommendations are easy to implement in our user-friendly console and you can learn more through the Fastly Academy.
If you are interested in learning more about TAM services or want to explore more NGWAF capabilities, please reach out to your account manager for more. And if you want to share any additional ways you prep for Black Friday weekend, you can share them with us on Twitter and LinkedIn.

