Tendances et informations exploitables sur les attaques DDoS qui ont visé des applications en décembre 2024
Les attaques DDoS visant les applications représentent une menace importante pour toute application ou API accessible via Internet. Elles peuvent en effet perturber les performances et la disponibilité du service pour les utilisateurs finaux et, potentiellement, entraîner une perte de revenus pour les entreprises. Ces attaques ciblent spécifiquement les services de la couche 7, comme les applications web, avec l’intention d’épuiser les ressources d’un serveur grâce à volume relativement faible de requêtes HTTP intelligemment conçues. Contrairement aux attaques DDoS sur un réseau, qui visent à submerger l’infrastructure réseau avec des quantités massives de trafic, qui se mesure souvent en térabits par secondes (To/s), les attaques DDoS ciblant les applications exploitent des faiblesses dans le code de l’application ou la mise en œuvre du protocole pour perturber le service avec un trafic relativement plus faible. Elles sont ainsi plus difficiles à détecter, mais tout aussi dangereuses.
Fastly collabore à grande échelle avec des entreprises internationales et utilise la télémétrie de son infrastructure mondiale et Fastly DDoS Protection pour détecter et atténuer le trafic des attaques. Dans ce rapport, Fastly présente des données anonymisées, des informations et des conseils exploitables sur les dernières tendances en matière d’attaques DDoS sur les applications pour vous aider à renforcer vos mesures de sécurité.
Principaux résultats
D’un mois sur l’autre, Fastly a observé une augmentation de 249 % du volume des requêtes associées à des attaques DDoS.
Les entreprises ont observé moins d’activité DDoS lors des week-ends (samedi et dimanche, heures UTC).
Pratiquement la moitié des attaques détectées visaient des entreprises des médias et des divertissements, suivies par celles des secteurs de la haute technologie et du commerce.
Tendances du trafic
En décembre, Fastly DDoS Protection a détecté plusieurs milliards de requêtes liées à des attaques DDoS sur des applications (Image 1).
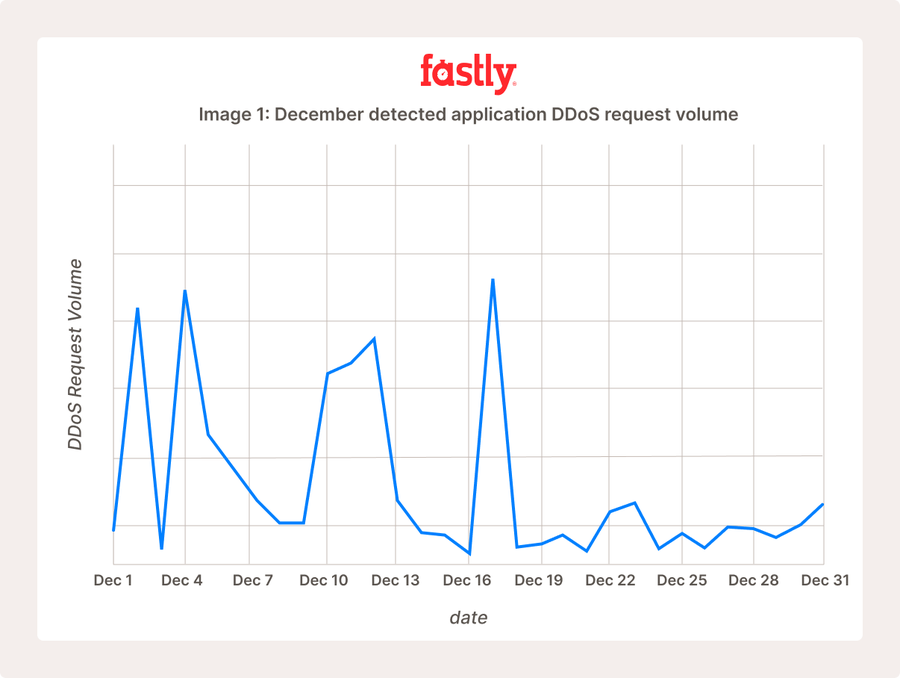
Si on les compare au volume global des attaques DDoS observées en novembre 2024, les requêtes associées à des attaques ont été 2,5 fois (249 %) plus nombreuses en décembre. Sur l’image 1, on remarque que 6 journées présentent un pic du nombre d’attaques par rapport au reste du mois de décembre. Ces 6 journées représentent 62,5 % du volume des attaques du mois entier. Si l’on regarde de plus près, pour 5 de ces 6 journées, le pic est principalement dû à une augmentation de 77 % du nombre d’entreprises attaquées. L’exception ? Le 4 décembre. Ce jour-là, le nombre d’entreprises attaquées a été inférieur de 38 % à la moyenne du mois, mais les attaques ont été beaucoup plus importantes.
Ralentissement dû aux fêtes de fin d’année et pauses pendant les week-ends
Alors que le début du mois avait connu une activité importante, le volume du trafic des attaques a considérablement chuté au cours de la deuxième quinzaine, ce qui indique peut-être que les hackers, comme nombre d’entre nous, ont aussi pris des congés pendant les fêtes. Si l’on compare la première et la deuxième moitiés de décembre, on constate une diminution d’environ 60 % des requêtes d’attaque observées (Image 2).

En examinant le nombre cumulé d’attaques DDoS sur un service, plutôt que le simple volume de requêtes qu’il contient (Image 3), on observe la même tendance à la baisse dans la deuxième moitié du mois.
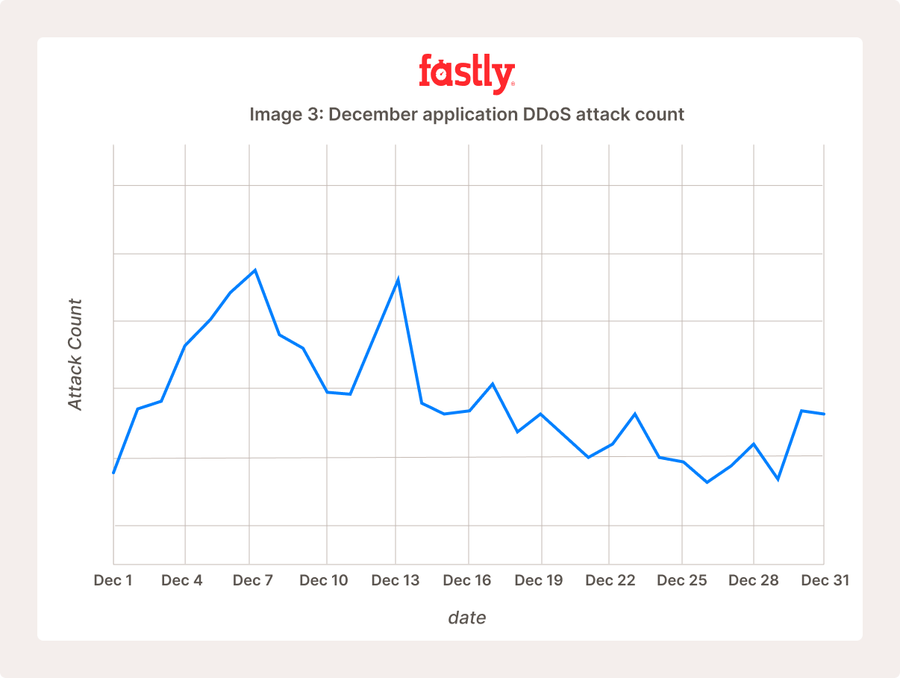
Cela conforte l’idée que les hackers font une pause pendant les fêtes au lieu de lancer leur flot d’attaques habituel. Il existe une autre explication : l’opération Poweroff pourrait avoir contribué à la différence notable d’activité DDoS constatée pendant la deuxième quinzaine du mois. Le 11 décembre, Europol a annoncé que l’opération en cours avait permis de saisir 27 des plateformes d’attaques DDoS les plus populaires utilisées pour lancer des attaques. Fastly va continuer à surveiller cette tendance au mois de janvier.
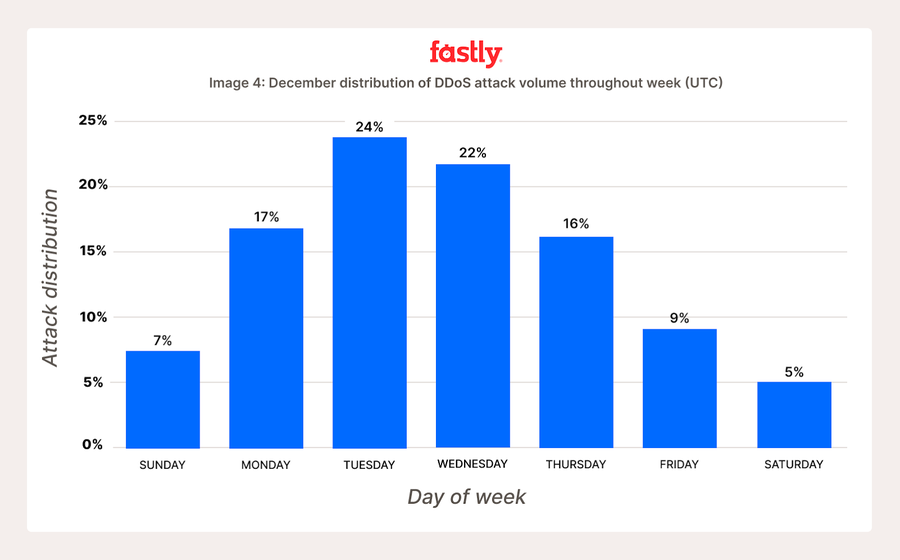
Non seulement les hackers ont pris des congés pendant les fêtes, mais leur activité s’est également notablement ralentie pendant les week-ends du mois de décembre. C’est lors des samedis et des dimanches (heures UTC) que le plus faible nombre de requêtes DDoS a été détecté. En fait, les entreprises ont été moins susceptibles de subir des attaques DDoS le week-end, avec seulement 12 % des requêtes de la semaine se produisant le samedi et le dimanche (voir Image 4). Les hackers préfèrent peut-être frapper lorsque les sites web connaissent le plus de visiteurs, et ce afin de maximiser les perturbations lorsqu’elles dérangent le plus.
Tendances en matière d’entreprises
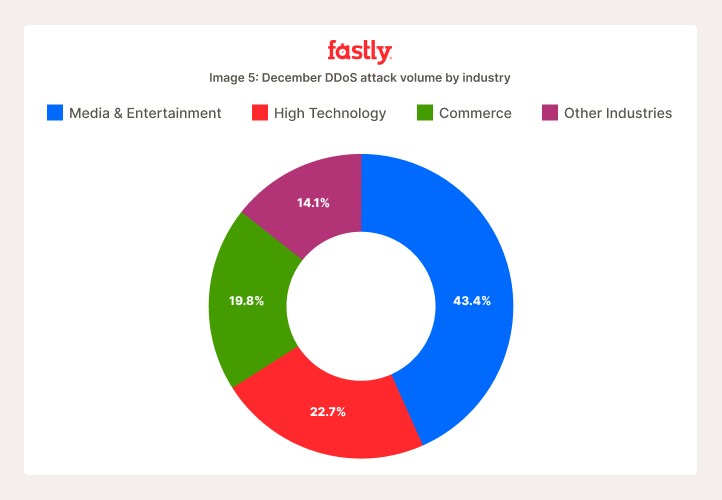
Si l’on examine les attaques DDoS de décembre en fonction du type d’entreprises attaquées, les requêtes DDoS se concentrent sur trois secteurs : Médias et divertissements, haute technologie et commerce (Image 5). Parmi les autres entreprises attaquées, on peut citer celles du secteur public, de la santé et des services financiers.
Mais quelle était la taille de ces entreprises ? Si vous ne travaillez pas pour une entreprise figurant dans le classement de Fortune, devriez-vous vous inquiéter des attaques DDoS sur les applications au vu des statistiques du mois de décembre ? Oui. Nous avons corrélé le nombre d’attaques DDoS sur des applications subies en décembre par les entreprises à leur chiffre d’affaires annuel estimé. Pour faciliter la visualisation, nous avons réparti les chiffres d’affaires en quatre groupes :
Grandes entreprises : Supérieur à 1 milliard $
Entreprises commerciales : Entre 100 millions et 1 milliard $
Petites et moyennes entreprises (PME) : Inférieur à 100 millions $
Non communiqué : Les entreprises pour lesquelles Fastly n’a pas pu déterminer de chiffre d’affaires annuel. Elles se situent probablement dans la fourchette des PME ou des entreprises commerciales, puisqu’elles n’ont pas publié d’informations ou alors sous forme restreinte(Image 6).
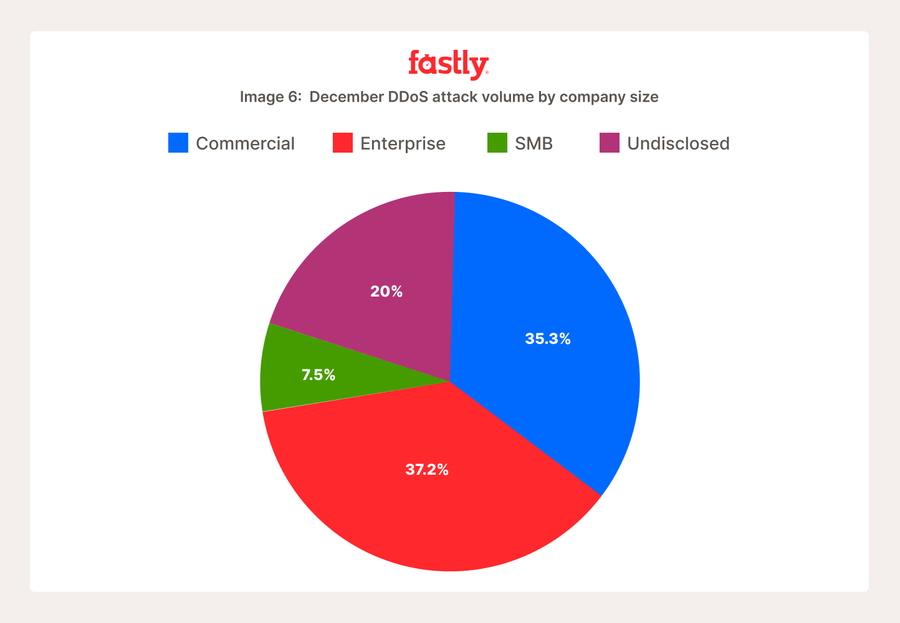
Même les plus petites entreprises subissent des attaques DDoS sur des applications, en particulier si une partie de la catégorie « Non communiqué » peut, de façon hypothétique, leur être attribuée. Quand le chiffre d’affaires annuel d’une entreprise dépasse le seuil de 100 millions $, les hackers les traitent de façon similaire, avec pratiquement les mêmes pourcentages d’attaques en décembre.
Conseils exploitables
Que pouvez-vous tirer de ces informations ?
Il est important de comprendre que ces données ne représentent qu’un seul mois. Elles doivent donc être utilisées en y associant les informations tirées de vos propres outils d’observabilité et des études à plus long terme pour créer un état des lieux complet. Cependant, il est possible de tirer quelques enseignements de ces données, que vous pourrez intégrer dans vos mesures de sécurité existantes :
Les entreprises doivent disposer de personnel dans leur centre d’opérations de sécurité (SOC) 24 h/24, 7 j/7. Cependant, d’après les données de décembre, c’est lors des jours de la semaine (heures UTC) que la présence de personnel est la plus importante.
Les entreprises opérant dans les secteurs des médias et des divertissements, de la haute technologie ou du commerce doivent être particulièrement attentives à leur système de défense contre les attaques DDoS visant les applications. Cela est particulièrement important au vu de l’augmentation du volume des attaques et de l’importance de la disponibilité des services pour atteindre les objectifs commerciaux.
Les entreprises de toutes tailles doivent s’assurer qu’elles disposent des outils pour se protéger contre les attaques DDoS visant les applications. Les grandes entreprises et les entreprises commerciales sont les plus susceptibles d’être frappées et doivent s’assurer de disposer de solutions robustes capables de gérer une augmentation de volume régulière. Cependant, même les PME sont visées et elles doivent mettre en place un certain niveau d’outils. Chaque application et chaque API présentes sur Internet sont susceptibles d’être la cible de ce type d’attaque à un certain niveau.
Atténuez automatiquement les attaques distribuées et perturbatrices
Fastly se doit bien sûr de vous rappeler que des solutions comme Fastly DDoS Protection stoppent automatiquement les attaques décrites dans ce rapport. Si le client avait été en mode de blocage, chaque requête associée à une attaque détectée aurait été bloquée. Fastly DDoS Protection utilise la bande passante élevée du réseau Fastly et ses techniques adaptatives pour garantir vos performances et votre disponibilité sans configuration. Contactez Fastly pour en savoir plus.



