Addressing PCI DSS 4.0 and Requirement 6.4.2
PCI DSS 4.0 requirement 6.4.2 forces organizations to procure and deploy a WAF by March 25, 2025. Fastly's Next-Gen WAF is the clear solution for organizations returning to a WAF after a hiatus or those using one for the first time.
On this page
Major credit card companies, including Visa, MasterCard, and American Express created the Payment Card Industry Data Security Standard (PCI DSS) to protect cardholder data. PCI DSS provides a comprehensive framework for securing payment card information throughout its lifecycle, from data entry to storage and transmission, and impacts all entities accepting or processing payment cards.
The PCI Security Standards Council announced Version 4.0 on March 31, 2022 with requirements that become largely effective on March 25, 2025. The updated version offers additional technical and operational requirements designed to protect account data and fill areas of weakness identified in its former version (3.2.1). A significant update to the standard comes via requirement 6.4.2, forcing some organizations to adopt technology to enhance their application security.
What is PCI DSS 4.0 Requirement 6.4.2
Requirement 6.4.2 updates requirement 6.6 in the standard’s previous version (image 1).

Version 3.2.1 of the standard recommended web application firewalls (WAFs) and noted penetration tests as permissible. However, by March 25, 2025, all organizations abiding by PCI DSS must have a WAF in front of their public-facing web applications to detect and prevent attacks.
While 6.4.2 will necessitate additional budget allocation for a WAF if one isn’t in place already, this purchase may have additional implications if a legacy WAF vendor is chosen and challenging to adopt. Other WAFs will likely require organizations to budget for additional headcount and resources as they force DevSecOps teams to regularly triage false positives, tune thousands of rules, and attempt to extract insights. Worst of all, many legacy WAFs are known to block legitimate traffic or break applications, impacting the organization’s bottom line and reputation.
For those returning to a WAF after a hiatus or those using one for the first time, Fastly’s Next-Gen WAF is the clear solution for requirement 6.4.2.
Solving Requirement 6.4.2 with Fastly’s Next-Gen WAF
Requirement 6.4.2 outlines four minimum requirements, all of which, Fastly’s Next-Gen WAF easily exceeds:
Defined Approach Minimums | Solution |
|---|---|
Is installed in front of public-facing web applications and is configured to detect and prevent web-based attacks. | Fastly’s Next-Gen WAF is the most flexibly deployed WAF on the market to protect everywhere your applications operate. |
Actively running and up to date as applicable | Enable Fastly’s Next-Gen WAF to update automatically, ensuring it is always up-to-date. |
Generating audit logs | Analyze the Next-Gen WAF’s logs in Fastly’s analytics tools or pipe them to integrations with DevOps and DevSecOps tools like SIEM or SOAR platforms. |
Configured to either block web-based attacks or generate an alert that is immediately investigated. | Fastly’s Next-Gen WAF operates in logging or blocking mode, leveraging our threshold-based blocking approach to confidently move to blocking mode faster. |
Fastly’s Next-Gen WAF surpasses the minimum 6.4.2 requirements and provides advanced web application and API protection (WAAP) for your applications, APIs, and microservices. Its protection goes beyond OWASP Top 10 injection-style web attacks (which auditors will be looking for at a minimum), and provides coverage against advanced threats, including account takeover (ATO) via credential stuffing, malicious bots, API abuse, and more from a single unified solution.
For organizations adopting a WAF in preparation for requirement 6.4.2, the Next-Gen WAF represents a seamless transition to application security that is flexible, accurate, and easy to use.
Get a flexible WAF for requirement 6.4.2
Modern organizations run complex tech stacks that require flexibility, but legacy vendors often take a one-size-fits-all approach with their products. Where other vendors make it difficult to customize products to match your unique needs, the Next-Gen WAF adapts to your needs to meet you wherever you are. Deploy it into nearly any environment, integrate it with dozens of your favorite DevOps and Security tools, and customize it to fit your unique security needs. While other WAFs force organizations can only deploy under specific architecture requirements, the Next-Gen WAF’s flexibility ensures it can integrate into any stack without creating silos in your DevSecOps pipeline.
Get an accurate WAF for requirement 6.4.2
When security teams want a WAF offering advanced protection without unnecessary toil, they choose Fastly. The Next-Gen WAF’s proprietary SmartParse technology enables highly accurate decisions resulting in fewer false positives than other solutions. The Next-Gen WAF’s detection is so accurate it requires only a fraction of the internal resources to operate, and it’s a major reason why almost 90%1 of our customers run it in full-blocking mode, whereas the industry average is far less. While other WAFs will steal security professionals' time for regular triage of false positives and tuning, the Next-Gen WAF’s accuracy enables organizations to spend fewer resources triaging alerts and more time on critical initiatives that drive their business forward.
Get an easy-to-use WAF for requirement 6.4.2
Procuring a WAF is the first step to adhering to requirement 6.4.2, and the decision carries long-term impacts on Security teams. While legacy vendors detect and block via thousands of rules security teams must manage and tune, Fastly’s Next-Gen WAF takes an entirely different approach.
Instead of blocking using tedious regular expressions like many legacy WAF vendors, Fastly’s Next-Gen WAF leverages SmartParse to offer Signals (image 2).
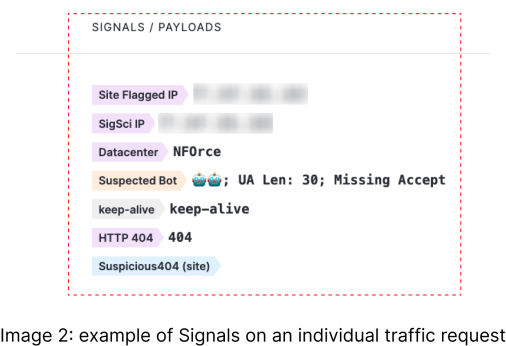
Signals provide clear guidance on what is an attack and integrate with our intuitive tooling to take action against them via alerts or blocking. Organizations leverage Signals with our threshold-based blocking methodology to limit the likelihood of blocking decisions impacting legitimate traffic. This departure from legacy methodologies enables organizations to move into blocking mode and gain confidence in their decisions before moving to instant blocking over time. Other WAFS make it difficult to validate blocking decisions leading to unintentional impacts on legitimate traffic, but the Next-Gen WAF offers insights and tools to easily protect your organization without impacting legitimate traffic.
Make the right choice for requirement 6.4.2 and beyond
Fastly’s Next-Gen WAF is the clear choice for organizations adopting a WAF to adhere to the new 4.0 requirements like 6.4.2 and helps solve existing requirements like 6.4.1 and 6.3.3. Its robust capabilities and easy-to-use functionality enable organizations to easily protect their apps, APIs, and microservices regardless of expertise or resources. Contact us to see a demo or learn more about how Fastly can help solve PCI DSS requirements.
1: Almost 90% of Next-Gen WAF customers run in full-blocking mode as of March, 2023
Meet a more powerful global network.
Our network is all about greater efficiency. With our strategically placed points of presence (POPs), you can scale on-demand and deliver seamlessly during major events and traffic spikes. Get the peace of mind that comes with truly reliable performance — wherever users may be browsing, watching, shopping, or doing business.
410 Tbps
Edge network capacity1
150 ms
Mean purge time with Instant Purge™
>1.8 trillion
Daily requests served4
~90% of customers
Run Next-Gen WAF in blocking mode3
As of December 31, 2024
As of December 31, 2019
As of March, 2023
As of July 31, 2023