What is web application security?
Web application security is the process of protecting websites and web-based applications from security vulnerabilities and attacks, ensuring that the application is free from vulnerabilities that could allow hackers to access sensitive data, steal information, or disrupt the application’s functionality. It involves implementing measures to prevent unauthorized access and protect against the loss or theft of sensitive data.
Developing web applications is ultimately a human-driven process, so it’s expected that web applications would inevitably contain bugs and misconfigurations, which malicious actors actively seek to exploit. Web application security helps address these vulnerabilities by leveraging secure development practices, implementing security testing throughout the software development lifecycle (SDLC), resolving design-level defects, and avoiding security concerns during deployment and runtime.
Why is Web Application Security Important?
Web applications are built to store, process, and transmit sensitive data, which makes them a prime target for hackers or other malicious actors to exploit. An unsecured web application could result in losing or stealing sensitive data, downtime, or “broken” apps. The consequences include traffic reduction, lost sales, broken customer trust, or government fines under applicable laws.
The most common web application security risks include the following:
Credential stuffing: This attack involves using a list of stolen credentials (usernames and passwords) to attempt to gain unauthorized access to various online accounts.
Injection: This attack involves injecting malicious code into a web application. The attacker can do this through SQL injection or other injection attacks.
Session hijacking: This attack involves taking over an active user session to gain unauthorized access to a web-based application. Techniques included are IP spoofing, sidejacking, man-in-the-middle, and session fixation.
Cross-site scripting (XSS): This attack involves injecting malicious code into a web page that gets executed by the browser of the person visiting the page.
Cross-site request forgery (CSRF): This attack involves tricking a user into submitting a malicious request to a web application.
Sensitive data disclosure: This is also known as data leakage or data exfiltration and can happen through a variety of channels, including email, cloud storage, social media, or through a data breach.
Broken authentication and session management: This attack exploits vulnerabilities in how a web application manages authentication and session information.
Security misconfiguration: This attack exploits configuration vulnerabilities in a web application.
Brute force: This attack involves attempting to guess a password or other authentication credentials by systematically trying every possible combination of characters. Usually, this is done with automation software until the correct combination is uncovered.
The top web application security vulnerabilities
The OWASP Top Ten lists the most common and critical security risks to web applications today. It’s published by the Open Web Application Security Project (OWASP), an organization dedicated to improving web application security.
Security communities in the public and private sectors have utilized the OWASP Top 10 as a guidepost for developing a unified set of practices and safeguards against common attacks and exploits. By understanding and addressing these risks, organizations can significantly improve the security of their web applications.
The OWASP Top Ten is updated every few years to reflect the current state of web application security. These risks are ranked based on their prevalence, the damage they can cause, and how easy they are to exploit. It's important to note that this is not an exhaustive list and that organizations must still be aware of and protect against other security risks.
The current OWASP Top Ten (2022):
Injection
Broken Authentication and Session Management
Cross-Site Scripting (XSS)
Insecure Direct Object References
Security Misconfiguration
Sensitive Data Exposure
Cross-Site Request Forgery (CSRF)
Using Components with Known Vulnerabilities
Insufficient Logging and Monitoring
Failure to Restrict URL Access
How to protect web applications
Protecting web applications from security threats involves a combination of toolsets, services, training, staffing, and policies throughout the engineering organization.
Protecting web applications is not just left to the security organization, as many companies don’t have the personnel or expertise to maintain a robust program. Modern development practices have started implementing security practices at the coding level, following it through to deployment, implementation, and maintenance after an application is released.
Organizations can take several measures to protect their web applications from security threats and minimize the risk of a data breach. However, it's important to note that no system is entirely secure, and it's essential always to be vigilant and to continuously monitor and update security measures to keep up with new threats.
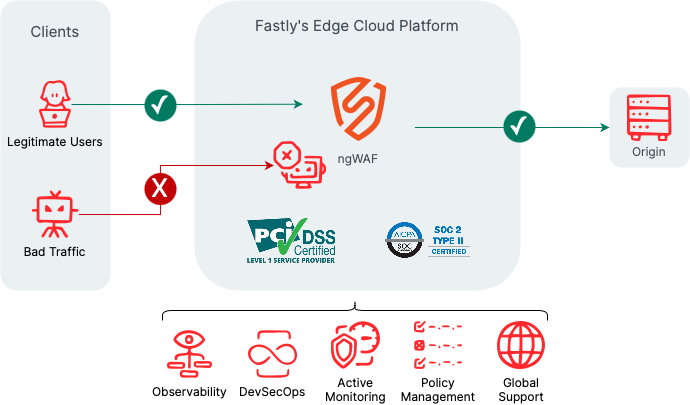
Steps organizations can take to protect their web applications:
Use a web application firewall (WAF): A WAF is a security tool that monitors and filters incoming traffic to a website, blocking malicious traffic and allowing legitimate traffic to pass through to the origin.
DDoS Mitigation: DDoS protection services use a network of servers in multiple locations to absorb and filter DDoS traffic before reaching the targeted website or network.
Enable HTTPS: HTTPS is a secure HTTP protocol to transmit data over the internet. Enabling HTTPS on your website or application helps to protect against data interception.
Use strong, unique passwords: Using strong, unique passwords for all accounts associated with your website and applications can help to prevent unauthorized access.
Keep software and plugins up to date: Outdated software and plugins can contain vulnerabilities that hackers can exploit. Keeping your website’s software and plugins up to date ensures you patch known vulnerabilities.
Monitor and log activity: Monitoring and logging activity on your website will help you identify suspicious activity.
Regularly scan for vulnerabilities: Regularly reviewing your website and application for vulnerabilities can help you identify and address potential security issues before attackers exploit them.
Train employees: Educating employees about security best practices can help to prevent accidental security breaches.
Implement security controls: Security controls such as input validation, output escaping, and error handling reduce the attack vectors that attackers can exploit.
Use secure coding standards: Have guidelines for designing and building applications and web properties. Perform regular code reviews to identify and fix vulnerabilities before releasing code.
Incident Response: Have an incident response plan to detect and quickly respond to security breaches.
Summary
Web application security is essential to ensure web applications' safety and sensitive data and must be a priority throughout the organization. By staying informed and proactive, teams can protect their web applications and data from potential attackers and prevent several consequences to their infrastructure, culture, and, ultimately, customer trust. An ounce of prevention is worth a pound of cure, and it’s always better to take preventative measures than to clean up the aftermath of a security breach.