What is TLS?
Transport Layer Security (TLS) is an Internet Engineering Task Force (IETF) standard protocol that provides authentication, privacy, and data integrity for communications over the internet. This protocol was published in 1999, and most recently, TLS 1.3 was published in 2018. An everyday use case of TLS is encrypting the communications between two systems. TLS is critical because it ensures the other party in a connection is who they say they are, illustrates whether data retains its integrity, and provides a level of confidentiality via encryption. TLS uses a range of different algorithms and methods to accomplish these purposes. It’s the most adopted and deployed security protocol in use today. It is best suited for web browsers and other applications requiring data to be securely exchanged over the network via Hypertext transfer protocol secure (HTTPS). TLS can also secure things like email and other protocols.
TLS vs. SSL
When discussing TLS, you will often mention Secure Socket Layer (SSL) or even SSL/TLS. SSL is the old version of TLS. Many in the industry still refer to TLS under its old name. The term TLS is used throughout the remainder of this article. It’s important to note that the names are often used interchangeably. TLS is the successor to the now-deprecated SSL.
TLS was born from Netscape’s Secure Sockets Layer (SSL) protocol and has superseded it. The protocol was rebranded as TLS to avoid issues with Netscape (still creating confusion today). With TLS being newer, most of the differences between the two are distinct. The maturity of the protocol has adjusted to address vulnerabilities and improve integration and implementation capabilities. Therefore TLS is more efficient and secure than SSL as it has stronger authentication, key generation, and support for different ciphers. TLS supports newer and more secure algorithms. The two are not interchangeable. However, TLS provides some backward compatibility for legacy capability. TLS handles the handshake much faster than SSL. In 2021 the IETF formally deprecated TLS 1.0 and 1.1, with major vendors, including Apple and Microsoft, following suit.
TLS vs. HTTPS
HTTPS is the secured version of the HypterText Transfer Protocol (HTTP). HTTP is the protocol used by your browser and web server to communicate and exchange information. When the data transfer gets encrypted with SSL/TLS, we call it HTTPS. Therefore, if your website uses HTTPS, all the information is encrypted by SSL/TLS certificates.
What does TLS do?
The TLS protocol achieves three primary components: Integrity, Authentication, and Encryption.
Integrity: confirms that the data sent across a network is not compromised.
Authentication: certifies the identities of the communicating parties are who they say they are.
Encryption: disguises the data transferred from third parties.
How does it work?
You can break the TLS protocol into two layers.
The TLS record protocol secures applications data using the keys created during the TLS handshake. The record protocol is responsible for securing application data and verifying it’s integrity and authenticity. The TLS handshake protocol is responsible for the authentication and key exchange necessary to establish and secure sessions.
The TLS record protocol provides connection security, and the TLS handshake protocol enables the client and server to authenticate each other and negotiate security keys before data exchange.
The TLS handshake is a multi-step process. The standard TLS handshake involves the client and server sending “hello” messages, exchanging keys, cipher messages, and a finish message.
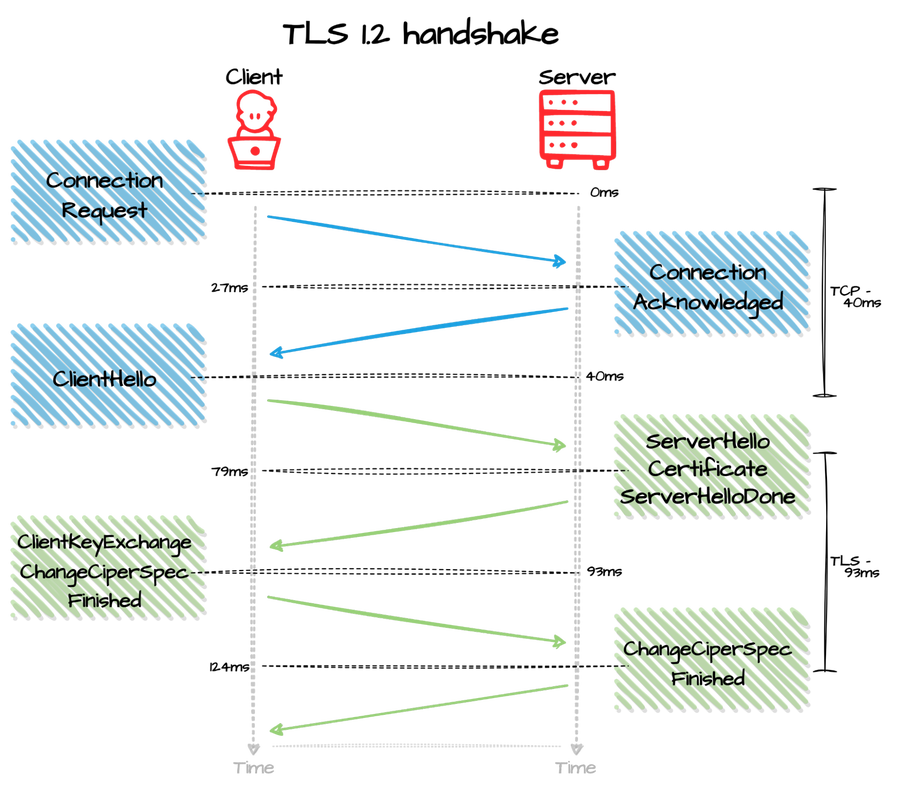
Does TLS affect web application performance?
Almost every website supports TLS 1.2, and nearly 60% (as of the publishing date) also supports TLS 1.3. TLS 1.3 brings significant security improvements and removes old weaker features. New features in TLS 1.3 help speed up the TLS handshake. Session Resumption checks to see if a server and client have communicated prior if they have some security checks omitted. False Start allows servers and clients to transmit data before the handshake finalizes. A TLS 1.3 handshake requires only one round trip instead of the previous two used in prior TLS versions. Lastly, Zero Round Trip Time Resumption (0-RTT) enables the generation of a master resumption key.
Using TLS also offers many benefits for businesses and web applications, such as improving your site’s Search Engine Optimization (SEO) and building customer trust. This way, it may help your business stay competitive in search engine results pages (SERPs).
Enable TLS today
TLS encryption helps protect web applications from data breaches and other vulnerabilities. Fastly TLS allows customers to manage TLS certificates on a domain-by-domain or multi-domain basis using our web interface or API. With Fastly TLS, you can either generate and upload your own TLS certificates and private keys or instruct Fastly to automatically generate and manage TLS certificates via a third-party, non-profit, or commercial CA on your behalf.
Suppose you need a specific Certificate Authority (CA) or need an Organization Validation (OV) or an Extended Validation (EV) certificate. You can use the Fastly web interface or API to upload TLS certificates and keys if you bring your certificates.
When Fastly manages your certificates, you use the Fastly web interface or API to select the CA from which Fastly should proctor your TLS certificates. Fastly then procures Domain Validated (DV) certificates from your chosen authority. To complete a certificate request, you must prove that you control your domains in two ways. If you use a wildcard to cover all your sub-domains with one certificate, you must add a challenge token to your Domain Name System (DNS) records. Fastly will automatically respond to the HTTP challenge if you do not need a wildcard. Fastly installs TLS certificates at a shared set of IP addresses by default. When client requests get sent to Fastly, we select the correct certificates using the SNI extension of TLS that allows clients to present a hostname in the TLS handshake request.
Summary
TLS is a widely deployed security protocol that encrypts data from plaintext into ciphertext and vice versa. TLS provides data security and privacy through encrypted traffic, preventing hackers from exposing sensitive data.
If you need a hand understanding and configuring TLS, Fastly can help.
Try Fastly for free today!