What is API Security?
APIs allow software applications to interact with each other, and they are critical to modern software patterns, such as microservice architectures.
API security is the measures taken to protect APIs from unauthorized access, misuse, and attacks. Because APIs are commonly used and enable access to sensitive software functions and data, they are becoming an increasingly desired target for attackers.
API security is a critical component of modern web application security. API security is essential for protecting sensitive data, such as financial information or personal data, and preventing attacks that could compromise the integrity of the API and the systems it connects to. APIs are becoming more prevalent and used to power critical business processes and services, so they must be protected.
Why is API Security Important?
APIs allow businesses to integrate different systems and technologies by allowing various applications to communicate quickly, leading to more efficient and effective operations.
APIs, however, can also create potential security risks if they are not correctly managed and secured. Attackers have been known to exploit API vulnerabilities to gain access to sensitive data or inject malicious code into applications, leading to data breaches, system crashes, and other serious consequences.
API security is essential to ensure data and resources' confidentiality, integrity, and availability. With microservices and serverless architectures, almost every enterprise application depends on APIs for basic functionality. API security is a core part of modern information security, protecting North-South and East-West traffic between applications.
In addition, API security is also critical for compliance with regulatory requirements such as GDPR, HIPAA, and PCI DSS, which mandate strict security and privacy protections for sensitive data exchanges. Failure to comply with these regulations may result in legal and financial penalties.
REST API vs. SOAP API
Modern APIs are designed from two main architectural types:
REST - A Representational State Transfer (REST) API is a web service that uses Hyper Text Transfer Protocol (HTTP) requests to communicate and interact with web-based applications or services.
SOAP - A Simple Object Access Protocol (SOAP) API is a web service that uses Extensible Markup Language (XML) to communicate and exchange data between applications or services.
RESTful APIs are widely used for building web-based applications and services. They are platform agnostic, meaning developers can use them with any programming language or framework supporting HTTP requests. They are highly scalable and can simultaneously handle large requests from multiple clients. SOAP APIs are commonly used in enterprise environments where security and reliability are critical. They provide a standardized way of exchanging data between different systems and can handle complex operations and messaging patterns. They can also be more complex and heavyweight than other web services and may require additional processing overhead and network bandwidth.
What is the OWASP API Security Top 10?
The increased API-related security threats have prompted the Open Web Application Security Project (OWASP) to release a unique top ten list specific to APIs. The OWASP API Security Top 10 is a comprehensive guide to help organizations understand the risks and threats associated with their APIs and how to secure them. Here are the top 10:
API1:2023 Broken Object Level Authorization: Object level authorization is an access control mechanism that is usually implemented at the code level to validate that a user can only access the objects that they should have permission to access.
API2:2023 Broken Authentication: Authentication endpoints and flows must be protected. "Forgot password / reset password" should also be treated like authentication mechanisms.
API3:2023 Broken Object Property Level Authorization: When allowing a user to access an object using an API endpoint, it is crucial to validate that the user has access to the specific object properties they are trying to access.
API4:2023 Unrestricted Resource Consumption: Satisfying API requests requires resources such as network bandwidth, CPU, memory, and storage. Service providers sometimes make necessary resources available via API integrations and pay-per-request, such as sending emails/SMS/phone calls, biometrics validation, etc.
API5:2023 Broken Function Level Authorization: The best way to find broken function level authorization issues is to analyze the authorization mechanism deeply.
API6:2023 Unrestricted Access to Sensitive Business Flows: An API Endpoint is vulnerable if it exposes a sensitive business flow, without appropriately restricting the access to it.
API7:2023 Server-Side Request Forgery: Server-Side Request Forgery (SSRF) flaws occur when an API fetches a remote resource without validating the user-supplied URL. It allows an attacker to coerce the application to send a crafted request to an unexpected destination, even when protected by a firewall or a VPN.
API8:2023 Security Misconfiguration: The API may be vulnerable if security hardening is missing, the latest security patches are missing, there are discrepancies in how incoming requests are processed, Transport Layer Security (TLS) is missing, etc.
API9:2023 Improper Inventory Management: The sprawled and connected nature of APIs and modern applications brings new challenges. Organizations need to have a good understanding and visibility of their APIs and API endpoints and how they store or share data with external third parties.
API10:2023 Unsafe Consumption of APIs: Developers tend to trust data received from third-party APIs more than user input. This is especially true for APIs offered by well-known companies. Because of that, developers tend to adopt weaker security standards, for instance, regarding input validation and sanitization.
API Security Best practices
API security best practices are essential to ensure secure and private service communication. Some of the best practices are as follows:
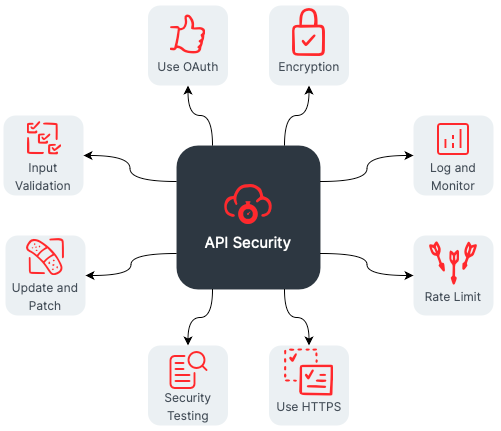
Use HTTPS: Always use HTTPS instead of HTTP. HTTPS provides encryption for data in transit, preventing man-in-the-middle attacks.
Use authentication: Implement authentication mechanisms to ensure only authorized users can access the API. Consider using OAuth or a token-based authentication solution.
Use encryption: Always use encryption methods to protect the confidentiality of your data. Use SSL/TLS or Advanced Encryption Standard (AES) level encryption.
Use rate limiting and throttling: Set rate limits on the method and frequency of API calls to prevent denial of service (DoS) attacks. Rate limiting can also balance access and availability by regulating user connections.
Use message-level security: Protect the integrity and confidentiality of messages. Consider using XML Encryption and an XML signature.
Use Input Validation: Validate all input data to prevent attacks such as a SQL injection (SQLi) or cross-site scripting (XSS)
Use role-based access controls (RBAC): Implement RBAC to restrict access to sensitive data or functionality.
Log and monitor: Implement a real-time logging and monitoring mechanism to detect and respond to security incidents.
Keep software up-to-date: Keep all software, including operating systems (OS), web services, and web application frameworks, up to date with the latest security updates and patches.
Security Testing: Conduct regular security testing to identify vulnerabilities and potential security risks.
Following these security best practices can help ensure your API endpoints stay secure and protected against attacks.
Try Fastly for free today!