What is a bot?
They’re everywhere!
Bots are the unseen driving force behind much of today’s internet, and we feel their impacts (both good and bad) worldwide. From crawler bots that make popular search engines like Google possible to credential-stuffing bots trying to access your accounts for sensitive information, at least 40% of all web traffic is attributed to bots. In this article, we will explore the world of bots - what they are, how they work, and where they’re headed.
Bots, short for robots or sometimes called internet bots, are software programs designed to perform automated tasks on the internet. They can be programmed to automatically crawl websites for data, interact with users through chat interfaces, fill out forms, and/or perform repetitive tasks. Bots typically perform tasks humans can do, but they are far more efficient, accurate, and functional at a scale larger than humans, thus exemplifying their prevalence.
Who bots are used by
Bots were once only accessible to those with the development expertise required to build them. Today they can also be purchased outright through legitimate organizations, marketplaces, or even the dark web to help individuals and organizations achieve their goals. Anyone with the technical know-how or enough money can use them to carry out legitimate or malicious actions. Bots can be:
Web crawlers that search engines use to discover, crawl, and index web pages on the internet.
Account scraper bots that automate the process of using stolen login credentials to gain unauthorized access to user accounts on various platforms.
Click-fraud bots that simulate clicks on online advertisements to artificially inflate ad revenue or sabotage competitors' advertising campaigns.
There are dozens of bot types and you can explore them here.
Legitimate vs. malicious bots
As we set the stage for bots, it’s important to note that they’re often classified as legitimate or malicious. While both operate on the same capabilities, legitimate bots are used for legal and/or ethical tasks, and you likely use them daily! Google and nearly every other search engine utilize crawler bots to find and serve you the best results for your search, and assistants like Alexa and Siri are examples of chatbots that help you perform many tasks. The lives of many rely on translation bots to help them read content in other languages, financial bots that help navigate the stock market, or many others that facilitate our modern lives.
In contrast, malicious bots (sometimes referred to as bad bots) are not only those involved in illegal cybercrimes but also those that don’t follow an application’s Terms of Service or robot.txt rules for behavior. Although the latter isn’t inherently illegal, unethical actions like these violate the site owner’s intentions, and thus, we classify those bots as malicious too. Malicious bots account for a staggering amount of the traffic we see on the web. For context, in Q3 2020 alone, malicious bots launched over 1.3 billion attacks! That’s over 15 million attacks daily for those counting!
How malicious bots are used
Malicious bot attacks strike with the ultimate goal of causing harm to organizations or individuals for the hacker’s gain. While malicious bots are broken into numerous types, many are used to gain access to sensitive information or disrupt normal organization operations.

Malicious bots can steal personally identifiable information (PII) such as names, social security numbers, credit card numbers, usernames, passwords, etc. Think of a piece of sensitive data you access on your computer, and hackers are probably targeting it. Hackers use that information to make unauthorized purchases, gain access to private accounts, and even sell it on the dark web. As an example, try entering one of your passwords into haveIbeenpwned.com. This popular site scans the dark web for passwords sold in lists and shares when one you use is compromised.
Malicious bots may also disrupt the normal flow of business. Typically these attacks are orchestrated by hackers looking to gain notoriety or damage the organization’s ability to operate, which may result in lost sales or market reputation.
Hacktivists also launch malicious bots that often target government bodies or companies operating in contrast to their position. Most recently, in the Russia-Ukraine war, anti-Russian Belarusian hacktivists slowed Russian troops’ progression through bot attacks that ultimately compromised the railway system’s routing rendering them inoperable. Hacker groups like Anonymous are often referenced here too.
Be mindful that the reason for attacks is seemingly endless, and these are just a few examples of how they are used to achieve attackers’ goals. Check out the malicious bot types learning article to learn the most common bot types utilized today.
How malicious bot attacks are launched
You’re currently accessing this article from the front end of the Fastly website, whereas malicious bots access applications from a different point of view. Malicious bots are launched from command-line interfaces or from graphical user interfaces (GUI) that create user-friendly overlays from which even a novice hacker can launch attacks.
From a command-line interface, bots are coded with instructions and complete their tasks without accessing the internet as you or I would. If the bot extracts information, the results are displayed in this window too.
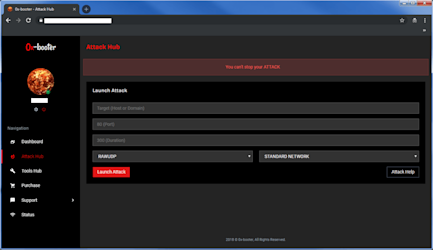
Launching an attack from a GUI platform is as straightforward as operating within any software. The interface tells you what inputs are needed, and with just the click of a button, you can launch an attack on the application of your choice. The example pictured below shows a purchasable DDoS-for-hire service that uses a botnet composed of tens of thousands of bots to launch attacks of at least 500 Gbps at a chosen application. To give a sense of scale - a high-volume DDoS attack is typically measured at 50 Gbps or more, meaning this service offers volumes ten times greater to anyone who can pay!
The future of bots
The continued advancement of AI and machine learning will feed the development of bots for all use cases. Bots that leverage the latest breakthroughs in these fields will look and act more human as they converse and/or automate tasks. For example, chatbots that utilize the latest advancements in natural language processing (NLP) and their large language models (LLM) will feel even more human-like as they respond to messages. We may even see a scenario where movies like Her come to fruition, and AI chatbots feel so real that humans fall in love with them (we’re not judging).
Breakthroughs in AI and machine learning also represent a massive concern for application security professionals because malicious bots will become harder to detect. Many trusted approaches to detecting and blocking malicious bots will be rendered obsolete against bots harnessing the latest technology - forcing security practitioners to rapidly adapt their approach to keep you safe. While we’re painting a dystopian future, the reality likely isn’t so bleak. In the cat-and-mouse game of security practitioners to hackers, technological advancements represent new cyber battlefields that both parties are trying to gain temporary dominance over. But while there may be some successful attacks by malicious bots, history has shown there isn’t a threat practitioners can’t contain in time.
The Automated Approach to Bot Management
Bad bots can negatively impact your bottom line and customer experiences. Fastly’s Next-Gen WAF acts fast to identify and mitigate bad bot activity, protecting your applications and APIs against various bot-driven malicious scenarios. It is the proven solution for organizations of all sizes worldwide. Explore its capabilities.