Beat the Clock: Your Guide to Meeting the PCI Compliance Deadline

シニアプロダクトマーケティングマネージャー、セキュリティ

Compliance is often seen as a roadblock or a necessary evil that slows down "real work" and stifles creativity. Who wants to spend their time making sure all the i's are dotted and t's are crossed when they could be doing things?
And yet, there's a small, but important set of people who actually like compliance. You might even call them compliance champions. They appreciate the clarity and structure that compliance brings, and they see the big picture in how rules protect users, employees, and the company. They find a certain thrill in uncovering a potential risk or finding a clever way to streamline a process while staying within regulatory lines.
Whichever side of the compliance coin you land on, there is no escape from it. And right now, time is running out to meet the requirements for PCI DSS 4.0 compliance.
Stopping client-side attacks
Modern digital experiences are powered by the interactions between web application servers and scripts that run on a user machine (also known as the client side). Web application developers often use common third-party scripts, code libraries, and dependencies to build their public-facing web applications.
There are many benefits to this approach for software teams:
It saves time and effort versus building applications from scratch
It unlocks third-party features that would not otherwise be available
It ensures the best compatibility across devices by using common building blocks
Unfortunately, using third-party scripts on your website means that you risk exposure to any security vulnerabilities that may exist within them. You need to trust that every script on your website is safe, even the ones you did not write yourself.
Security vulnerabilities in client-side scripts can leave your users vulnerable to client-side attacks. In this type of cyber attack, criminals quietly modify the code that executes on the client side at runtime to perform:
Cross-site scripting (XSS)
Payment card skimming
Social engineering and phishing attacks
And more
Payment card skimming, or Magecart-style attacks, is the digital version of attaching a hidden card reader to a retail point-of-sale terminal. Using known vulnerabilities, attackers inject malicious code into scripts used on e-commerce checkout pages to steal customer payment card information in real time. They can remain undetected for a long time and potentially compromise thousands of users.
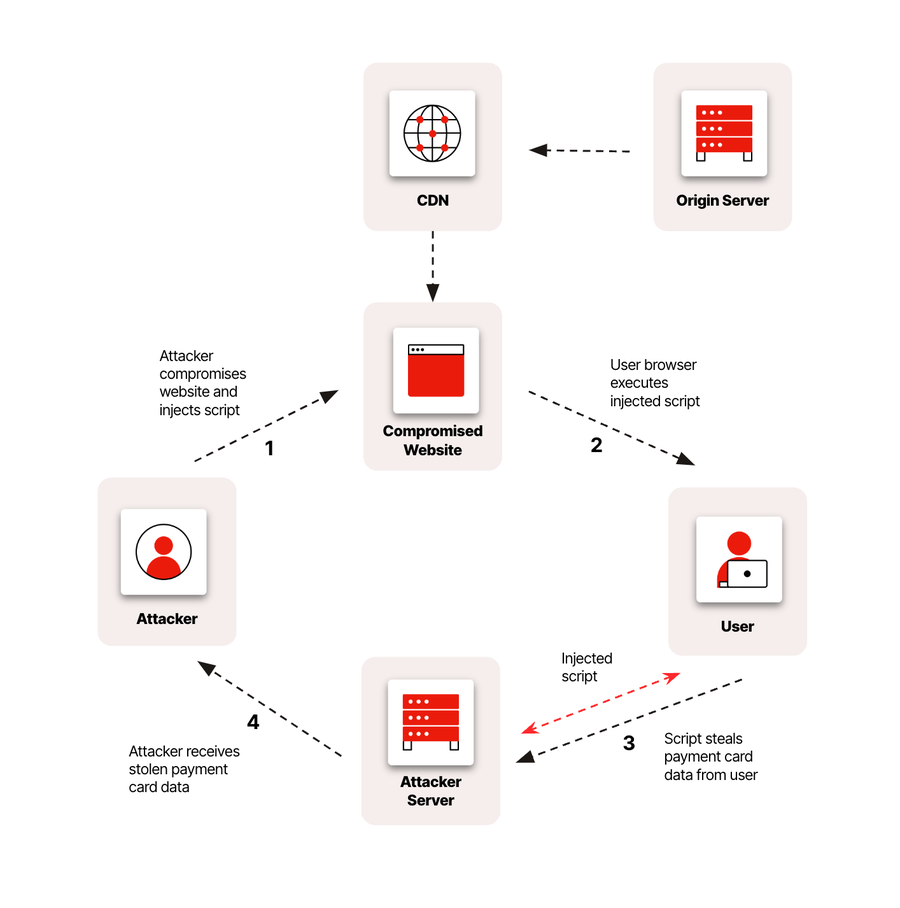
Fight back against payment card thieves
What can be done to stop this? As part of a holistic approach to application security, organizations should:
Adopt general secure software design practices
Deploy defense in depth on application servers
Deploy specific measures to detect and block client-side attacks
These practices align with the recommendations of leading cybersecurity organizations like the OWASP Foundation, CISA, NIST, and the PCI Security Standards Council.
As mentioned in our earlier blog, a major reason for the enhanced security measures in the latest Data Security Standard is the increase in attacks that steal payment card data.
The latest PCI DSS requirements (version 4.0.1) include several provisions specifically designed to mitigate the risk of payment card skimming:
Requirement 6.4.3
Maintain an inventory of all scripts used with written business or technical justifications for their use, and be able to confirm scripts are authorized and have not been compromised.
Requirement 11.6.1
Generate alerts if there are any unauthorized modifications to headers as received by the user browser, which could indicate scripts have been compromised.
To meet these requirements, organizations need to demonstrate that they have implemented technical solutions to accomplish these important goals:
Know exactly what scripts you have on your website and why they’re there
Make sure that those scripts are supposed to be there and are safe to use
Get notified quickly if anything looks suspicious
Time is running out - don’t delay!
PCI DSS compliance is forcing the issue for many organizations, but client-side attacks are about so much more. Thankfully, there’s good news for compliance procrastinators. Soon, Fastly customers will be able to do all of the above and fight back against client-side attacks with just a few clicks.
Fastly Client-Side Protection gives your teams the visibility they need to fully document, understand, and manage client-side attack surfaces in real-time to prevent the exfiltration and misuse of customer data. It helps you meet the PCI-DSS 4.0.1 requirements related to script inventory and management.
Best of all, it takes only minutes to generate your script inventory, and it’s easy to manage from within your existing Fastly dashboard. Your teams can spend less time worrying about compliance and get back to what they do best: building cool things.
If you’re interested in Fastly Client-Side Protection, contact us today and we’ll get you started.