In our previous installment of the Signals Series, we introduced and defined the concept of signals and how they play a key role in our award-winning Next-Gen WAF. Specifically, we walked through how custom signals can power better blocking decisions and take specific actions based on complex filtering and parameters.
Today we want to dive into the capabilities of system signals and how our wide range of signals provide you with the most comprehensive out-of-the-box application protection.
Exploring System Signals
As a refresher, Fastly defines signals as descriptive tags that our Next-Gen WAF can add to requests as they are inspected. Signals can be visualized in charts, queried in logs, and incorporated into rules. Our WAF signals fall under two categories: custom signals and system signals.
While custom signals provide in-depth capabilities tailored to your traffic, we want to empower those security and DevOps teams who need to identify attacks and protect their applications quickly. That’s where system signals come in.
System signals are our “out of the box” signals that assign a tag based on inspecting a client's request. With over three dozen system signals, the Fastly Next-Gen WAF has comprehensive coverage over the attacks and anomalies that matter most to security teams. The full list can be found here.
Sample listing of System Signals
Attacks |
|---|
Attack Tooling |
AWS SSRF |
Cross Site Scripting (XSS) |
Log4J JNDI |
GraphQL Max Depth |
Anomalies |
|---|
Abnormal Path |
Datacenter Traffic |
Duplicate Header Names |
Malicious IP Traffic |
SearchBot Imposter |
As you can see from the sample list, the Fastly Next-Gen WAF covers standard vectors like XSS and provides insight into potentially malicious IP traffic. But as tech stacks evolve and attack surfaces increase, the team also identifies more recent vulnerabilities such as Log4Shell and emerging technologies like GraphQL to ensure your coverage is up to date.
Signal Highlight: GraphQL
Developers are rapidly adopting GraphQL, an open-source standard query language, as an alternative to REST to meet the flexibility needed to maintain modern, high-growth APIs.
The Fastly Next-Gen WAF offers coverage that detects, inspects, and blocks OWASP-style injection attacks, denial of service (DoS) attacks, and other vulnerabilities that can target GraphQL APIs. With the addition of GraphQL Inspection, there are now GraphQL-specific signals in the console for customized protection based on user configuration. With these signals, you can define rules to route requests when certain thresholds or events happen. Some of these signals are included below.
GraphQL Max Depth: A request has reached or exceeded the maximum depth allowed on the server for GraphQL API queries
GraphQL Introspection: An attempt to obtain the schema of a GraphQL API. The schema can be used to identify which resources are available, informing subsequent attacks.
GraphQL Undefined Variables: A request made to a GraphQL API containing more variables than expected by a function
GraphQL Duplicate Variables: A request that contains duplicated variables
GraphQL Missing Operation Name: A request has multiple GraphQL operations but does not define which operation to execute
GraphQL IDE: A request originating from a GraphQL Interactive Development Environment (IDE)
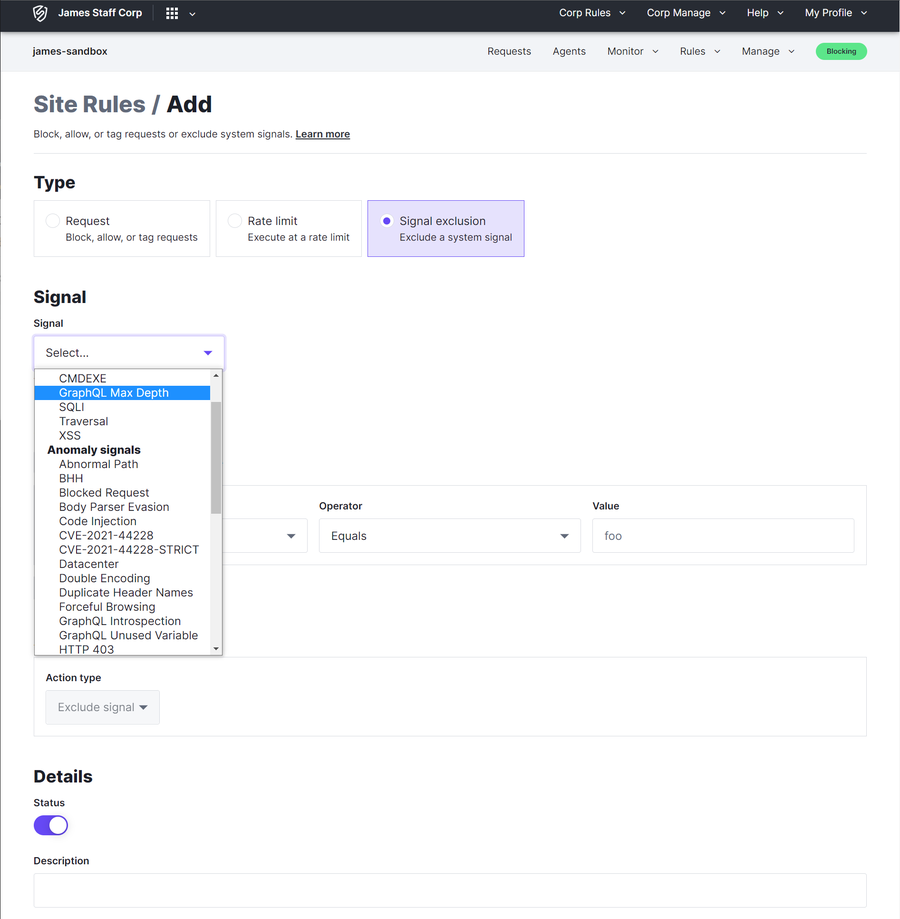
GraphQL-specific Signals can be used to create a Request, Rate Limit or Exclusion rules to a Corp or Site
Let’s take a look at an example of creating a Request Rule using the GraphQL Max Depth Signal to block traffic in order to avoid misuse or a potential DoS attack.
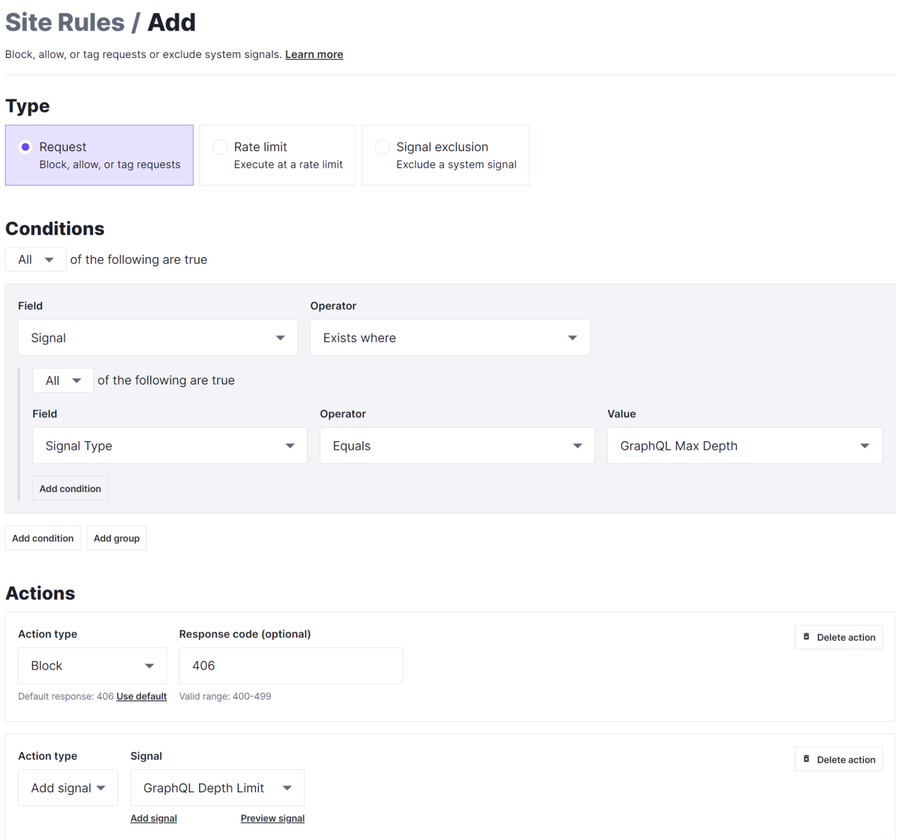
In the above rule we match on any requests that contain the “GraphQL Max Depth” signal and block them with the HTTP status code “406 Not Acceptable.”
Rejecting RegEx with SmartParse
SmartParse detection method
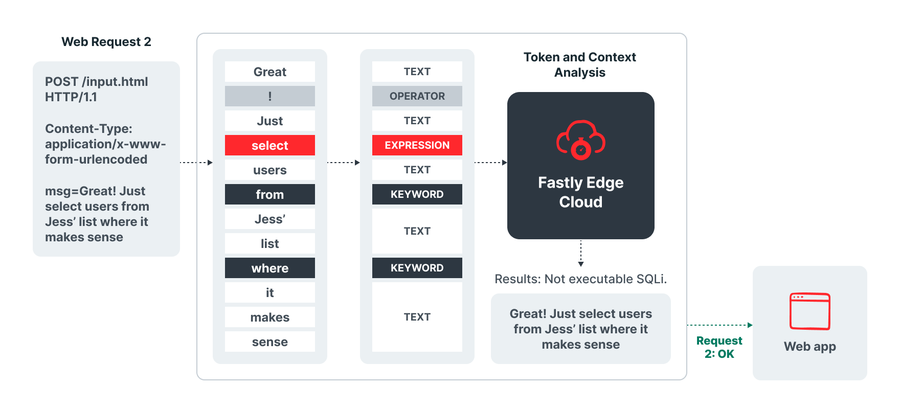
SmartParse tokenizes web requests to provide more accurate detections
System signals are powerful tools for our customers because they immediately identify the type of payload coming through the application. Teams can then display these signals on their dashboard or generate reports to get a comprehensive look at their application’s traffic trends.
But the power of these system signals is only as good as our ability to accurately inspect and identify that a payload contains an SQI or XSS attack. Failing to do so ultimately leaves applications vulnerable by letting attacks through or blocking legitimate customers.
Our Next-Gen WAF surpasses the attack detection ability of traditional WAFs because we’ve rejected regular expression (regex) as a detection method, and created a more powerful and accurate alternative called SmartParse.
Traditional WAFs have historically relied on regex to power their inspection and decision-making processes. However, if an e-commerce customer wants to buy a British flag, for example, the search term “union jack” could be flagged as a SQLi attack and a legitimate user potentially blocked. This leads to a lot of time wasted tuning for false positives and ultimately lowers the trust that you may have within your WAF.
Instead of just looking at strings, we created SmartParse to tokenize the request coming through and look at that hash to take a contextual understanding of the request. SmartParse confirms that a request is formatted to actually execute an attack, regardless of whether certain terms match common attacks or anomalies.
SmartParse is the heart of our product because it informs how our system signals deliver information to our customers. It lays the foundation of trust that customers have in our ability to deliver quick and accurate protection.
Where can signals take you?
We hope you enjoyed this two-part series on the Fastly Next-Gen WAF’s signals and how they transform your team’s ability to quickly and more accurately protect your apps and APIs. Our signals technology plays a key role in how security and DevOps teams understand what kind of traffic impacts their sites. With this kind of knowledge at your fingertips, who knows where our Next-Gen WAF can take you!
If there are other parts of our technology you want to get a deep-dive on, send us a message on Twitter or LinkedIn. And if you want to explore our Next-Gen WAF even more, click here to learn more about what else our web application and API protection can do for you.
