As organizations grow, it’s common for security administrators to have more applications to manage and have less communication with the primary application developers. This results in a few organizational challenges that evolve into potential security threats. Commonly, the security admins may not be aware of all of the application’s new features, such as new authentication endpoints, that they are tasked to protect. Security teams that inherit legacy applications may also experience knowledge gaps if there are no application developers remaining for a mission critical application. In these and other situations, it’s a question of visibility and awareness: how can the security admins protect what they do not even know about?
A precursor to protecting the vulnerable parts of the web application is collecting an inventory of what needs to be protected. After all, you cannot protect what you do not know about. Out of the box, Fastly’s Next-Gen WAF (NGWAF) provides protection against injection based attacks such as SQLi and XSS. Web and API login endpoints that may be vulnerable to attacks such as credential stuffing or credential cracking. We want to empower our customers to discover login and authentication endpoints before they are abused by cyber criminals.
Login Discovery Overview
Fastly is proud to announce the Login Discovery templated rule, which will help customers gather an inventory of their web and API endpoints that are likely to be associated with a login or authentication attempt.
While it is hard for security and fraud teams to have expertise on all of the functionality that exists in the applications that they are tasked to protect, this new templated rule surfaces these key functions and keeps security teams aware of authentication endpoints without disrupting the CI/CD workflow.
Thankfully web and API software developers are not typically forced to invent new authentication workflows for their applications that have never existed before. With this idea in mind, all we need to do is look at the request body using Fastly’s Next-Gen WAF SmartParse, to look for certain fields such as “password” and “username”. The templated rule will also look for paths such as “/login”. If you know your application uses other request body fields or other criteria, then you may customize the templated rule as well to suit your needs. Once the templated rule is enabled, any requests that match the condition will receive the Login Discovery signal.
Enabling and using Login Discovery
You may easily enable the Login Discovery templated rule via the User Interface or API. To enable the feature through the UI, navigate to Templated Rules and search for “Login Discovery” and click “view”.
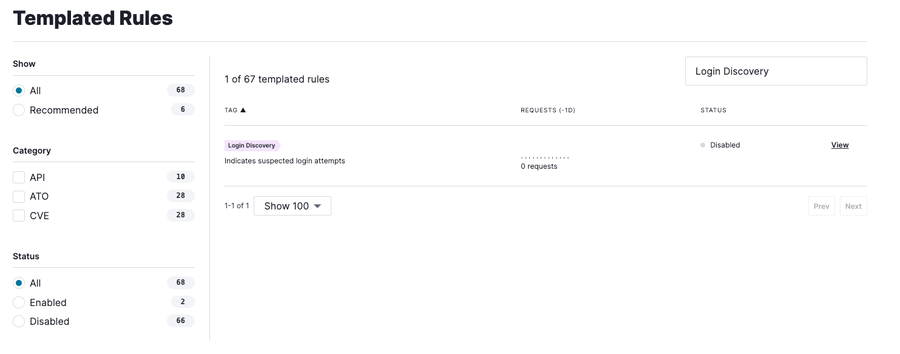
Then click Configure and click the enable button at the bottom of the page. From there, the Fastly’s Next-Gen WAF will find and display authentication attempts with the signal Login Discovery.
From there, customers can use this signal to take action, like creating a request rule or an advanced rate limiting rule for additional visibility into requests that match this signal or mitigate requests that match this signal with an action such as block.
We’re always looking for feedback from our customers, if you have any questions please reach out to us on Twitter or LinkedIn.
