The Back to Basics of Automated Attacks: A Primer
This is the first in a series of posts where we’ll cover the basics of various automated attacks on web applications, commonly known as bot attacks. In each post, we’ll provide an in-depth examination of the nature of the attacks, the motivations, discuss real-world examples, and techniques to mitigate them.
What is Account Takeover?
Account takeover (ATO) attacks are a form of online identity theft, where threat actors gain unauthorized access to a customer account (e.g.,online banking, email, e-commerce, social media accounts). The motivation of the actors can vary, from conducting fraudulent transactions to spreading misinformation during an election season. But the key objective of this attack is for the actor to gain the ability to operate a customer’s account, and hence the account’s entitlements. These attacks could be targeted to a specific customer account or could be a spray-and-pray against millions of accounts.
We have examined some of the common tools used in automation attacks in a previous post. In this post we will examine a few common types of ATO attacks such as Credential Stuffing, Account Aggregation, and Credential Cracking as well as the commodity tools specifically designed for these attacks.
Credential Stuffing
Credential Stuffing attack involves using a list of stolen credentials (i.e., usernames and passwords) a.k.a combos, to attempt to gain unauthorized access to an online account. This attack is feasible due to the common mispractice of credential reuse, where users, for the sake of convenience, end up using the same credentials on multiple accounts/websites. So when one of these websites is compromised and the unencrypted credentials of its users are leaked in underground forums, other actors make use of this list to conduct credential stuffing attacks on unrelated websites.
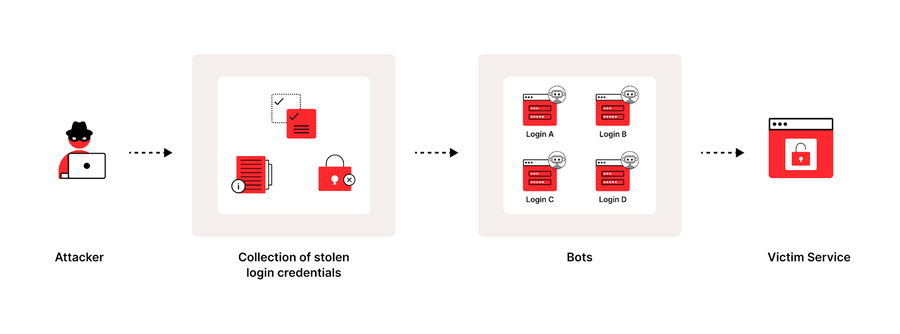
Figure 1: Bots submit stolen credentials to the victim service to check for valid logins
While this is a type of spray-and-pray attack, due to massive reuse of credentials, this has proven to be an effective low cost attack, with industry estimates of the success ratio at about 0.1%. While this seems like a low success rate, when millions of credentials are attempted on the target website, the threat actor likely gains access to thousands of accounts. As of June 2024, the HaveIBeenPwned dataset includes 936 million passwords, corresponding to 6.95 billion credentials.
Figure 2: Sentry MBA provides a number of features and settings to launch an attack
What makes this common is also the mature market economics for these types of attacks. A bad actor can purchase a combo list, tools to conduct the attack (such as SentryMBA, SNIPR, OpenBullet, BlackBullet, STORM, etc), and tool config for the targeted service quite cheaply from underground forums. Some of these tools even have additional add-ons one can purchase to defeat specific anti-bot features. The next step is to buy a proxy list from any of the scores of websites online, to be able to rotate the attacks over multiple source IP addresses. And you have now armed yourself with all the components required to conduct a credential stuffing attack. It’s also noteworthy to mention that there is a market to buy the breached credentials harvested from this attack, providing a strong economic motivation.
Figure 3: SNIPR has built in attack configs for popular websites
Account Aggregation
This is a form of credential harvesting attack, when customers end up using unauthorized clients, giving the client the opportunity to steal credentials or modify the request/response for malicious purposes. This is often found in the form of malicious third-party apps on app stores, or account aggregation websites which require users to submit credentials. These apps are not authorized clients of the website, yet they are commonly used for aggregating social media, email or financial accounts into a consolidated view.
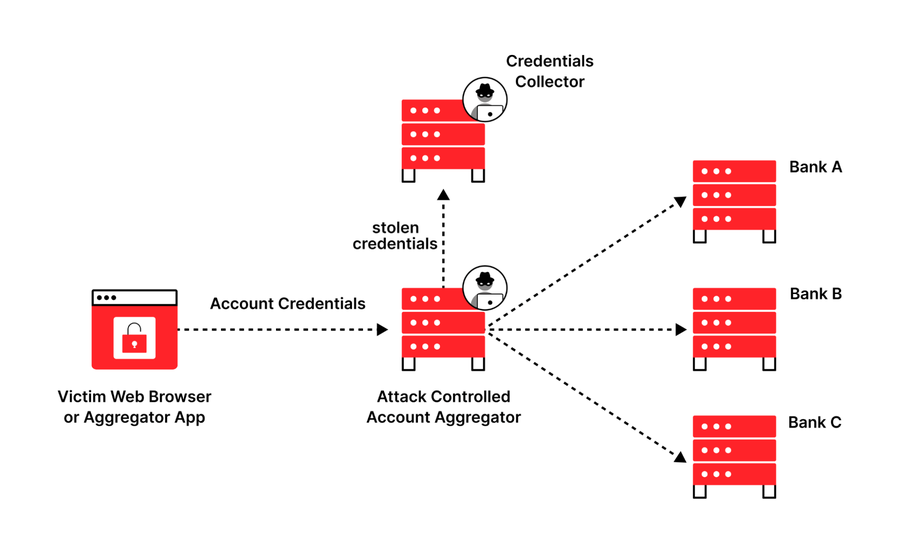
Figure 4: Credentials are stolen from a malicious/compromised account aggregator
While traditional credential harvesting attacks using phishing with an evil proxy achieve the same results, account aggregation attacks are more effective due to their persistent nature under the guise of being a genuine application.
Credential Cracking
Credential cracking is a bruteforce attack on a login endpoint, using a word list with the goal of identifying valid credentials. While this seems similar to credential stuffing (which is spray-and-pray), credential cracking often narrowly targets a specific account or type of account.
The attack is most effective against applications that are vulnerable to username enumeration. Once a valid username is identified, the password brute forcing attack is employed to determine valid credentials.
Attack Mitigation
Modern Authentication
Modern authentication methods, such as two-factor authentication (2FA) and passkeys, significantly enhance security by requiring more than just a password to access accounts.
2FA with proper registration and reset procedures, adds an extra layer of protection by combining something you know (a password) with something you have (e.g., a smartphone app based Push 2FA, hardware token) or something you are (biometrics like fingerprints or facial recognition).
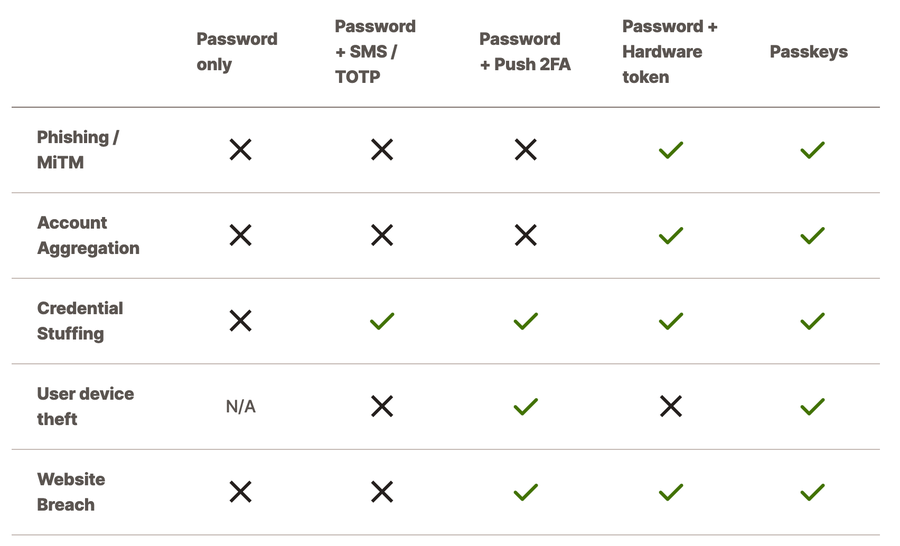
Table 1: Effectiveness of authentication methods against threats
It’s important to note that SMS or TOTP as a second factor, while cost effective, do not provide sufficient protection from evil proxy MiTM attacks as the token can also be relayed to the target website similar to the credentials.
Similarly, second factors using “Push 2FA” are vulnerable to MiTM and account aggregation attacks, as the second factor is validated out of band anyway. Hardware tokens have the issue of device theft, as they usually don’t require a biometric verification. So anyone in possession of the device can present them as the second factor. However, the need for physical proximity for device theft significantly reduces the risk, making it suitable for everyday use, especially considering its wide industry adoption.
On the other hand, passkeys, which are cryptographic keys stored on devices, eliminate the need for passwords altogether, providing a seamless yet highly secure authentication experience. Also, passkeys typically require biometric validation to be activated. While this method of sign-in is currently under adoption, we recommend using passkeys wherever they are supported. Watch our developer experience team explain the working of passkeys and WebAuthn, and implement them for your website, using Fastly Compute.
These methods mitigate the risk of account takeover by making it much harder for attackers to gain access, even if passwords are compromised. One of the key benefits of passkeys and hardware tokens (both implementing WebAuthn standards) is that the credential is tied to the website URLs during registration, making them resistant to phishing attacks. With these options an appropriate 2FA method can be chosen based on the sensitivity of the website.
Anti-Automation Controls
Anti-automation controls such as request analysis, user-agent integrity checks, crypto challenges, visual/audio challenges can be employed to identify if the request was initiated by a human at the other end or if it’s traffic generated by bots. Various forms of rate limits can also be used to mitigate or slow down automated attacks.
Compromised Credential Detection
Checking for use of compromised passwords is a very effective defense against credential stuffing. NIST guidance for “memorized secrets” recommends comparing passwords to “passwords obtained from previous breach corpuses” during login, signup, and password reset. We have covered this topic with a solution employing Fastly Compute and KV Stores in a previous post.
Education and Awareness
When password use is unavoidable, using a password manager, with auto-generated passwords could mitigate credential stuffing attacks, by simply preventing password reuse.
Implement passkeys and encourage users to adopt passkeys. Passkeys are a convenient alternative to passwords, and drastically improves account security.
User education about the risks involved in use of third-party apps and aggregators, reduces the risk of leaking credentials.
Provisioning API keys with limited access for use with third-party apps, prevents credential leaks, along with the opportunity for enhanced monitoring of requests from third-party apps.
A holistic approach to ATO mitigation
This post discussed some of the automated attacks employed for account takeover. But there are other forms of account takeover attacks, notably through session hijacking with XSS or credential harvesting through phishing; making it important to holistically address security risks. A combination of a traditional WAF, effective bot management, strong security practices and end user education is required to address account takeover risks.
References:
OWASP Automated Threats to Web Applications.
FIDO2 specification and overview of CTAP1 (a.k.a U2F), CTAP2 and WebAuthn

