TLS fingerprinting is one of many techniques used to identify malicious traffic for network defense. The technique has been used quite widely for almost a decade. Over the years, a number of TLS fingerprinting algorithms have been developed to identify clients and servers. You can read more about them in our earlier blog post.
On January 20th, Chrome shipped an update that changed the profile of one of the most popular TLS client fingerprinting algorithms, JA3. In this short blog post we’ll describe the change and our observations across Fastly's network.
TLS fingerprinting and the Chrome update
Fingerprinting TLS clients can be used to help classify traffic and identify network attacks. TLS client fingerprinting algorithms typically rely on inspecting the TLS ClientHello messages to extract specific attributes like the TLS version, the ciphers it supports, the supported elliptic curves, curve formats, and the list of TLS extensions sent by the client. JA3 is a widely used TLS fingerprinting standard, developed by researchers from Salesforce and adopted into a variety of commercial and open source tools. Most significantly for this post, the JA3 algorithm uses the TLS extension order sent by the client as a feature of the fingerprint it produces.
A recently implemented feature in the Google Chrome browser permutes the set of TLS extensions sent in the ClientHello message, resulting in a different JA3 fingerprint with every new connection from the browser.
This change was made to prevent servers from expecting a certain fixed order of extensions, which could limit Chrome from making future modifications to its TLS implementation, with a goal of making the TLS ecosystem more robust. If you’ve heard of TLS GREASE, this might sound familiar. It’s noteworthy to mention the TLS Version 1.3 RFC specifies that extensions may be sent in any order, except for the pre_shared_key which, if present, MUST be sent as the last of the extensions.
Given the number of permutations possible for TLS extensions sent by Chrome is nearly 15 factorial (about 10^12), we can expect each connection made with the TLS ClientHello extension permutation feature to practically have a unique JA3 fingerprint.
This feature was initially to be released in Chrome version 110, but seemed to have taken effect in versions 108 and 109 as well, beginning soon after the feature was enabled by default in Chromium source code.
Watching the change
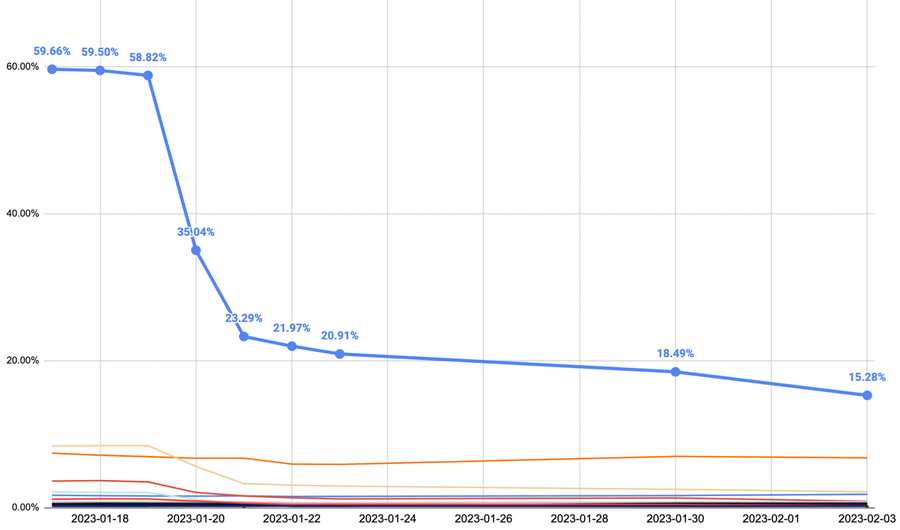
The most recent and common JA3 fingerprint of Chrome on most platforms was cd08e31494f9531f560d64c695473da9 before this change. Beginning on January 20th, 2023 we observed the percentage of Chrome clients connecting to Fastly's network with this fingerprint (depicted by the blue line in the chart below) drop off significantly. We expect the trend to continue as users update their browsers to include the extension permutation feature.
More to come
The extent of this change is limited to Chrome as of writing this, though Firefox is considering a similar feature in the future. While these TLS robustness improvements may change the utility of order-sensitive TLS fingerprinting techniques like JA3, new algorithms which account for randomized extension order may be developed.
In addition, organizations like Fastly are working together with the internet community to create technology like Private Access Tokens that provide open, privacy-respecting protocols. This technology provides immediate benefit for network defense, but may also eventually supplant passive fingerprinting techniques used to identify browsers.
If you would like to take action on JA3 hashes in Fastly’s platform, you can access them through VCL and Compute libraries.
Find out why Private Access Tokens will future-proof organizations & common CAPTCHA pain points.



