Security organizations are often the first to alert the market to changes in the application security landscape, citing its dynamic nature as a justification to buy their latest and greatest solution. It’s a given that change is real, and attackers are using the latest developments (insert AI quip), but ‘how is the industry adapting?’ is the real question we’re in search of, right? Knowledge is limited to what you can pull from those same AI tools and what your network is sharing on social media.
In an effort to explore how the industry is shifting, we’ve partnered with Informa TechTarget’s Enterprise Strategy Group to see how 383 cybersecurity and IT professionals at organizations across the United States and Canada are adapting. The findings highlight:
How fast the environments we’re working to secure are growing
Desire for consolidation
The need for automation in response to multi-pronged attacks
Use their combined perspective to gauge whether your security strategy is focused in the right areas.
The environments we protect are evolving faster
How we protect must be informed by what we’re protecting. As organizations increasingly rely on applications and APIs to generate revenue, the landscape continues to grow, but how fast? On average, the professionals surveyed noted they’re protecting 145 web applications and websites per organization and expect this number to grow to 201 on average in the next 24 months, a 39% increase. And what of the APIs that power the site’s unique experiences? Only 32% of the majority of their applications use APIs today, but they expect it to be 80% in the next 24 months.
The increase in volume, API adoption, and associated deployment velocity are causing concern for these professionals. When asked, “Which of the following challenges does your organization face in protecting its public-facing web applications?”, 32% noted that agile development processes are making it difficult to maintain security. The most common answer to the question (41%), was that the increasing use of cloud infrastructure was their biggest challenge (Image 1).
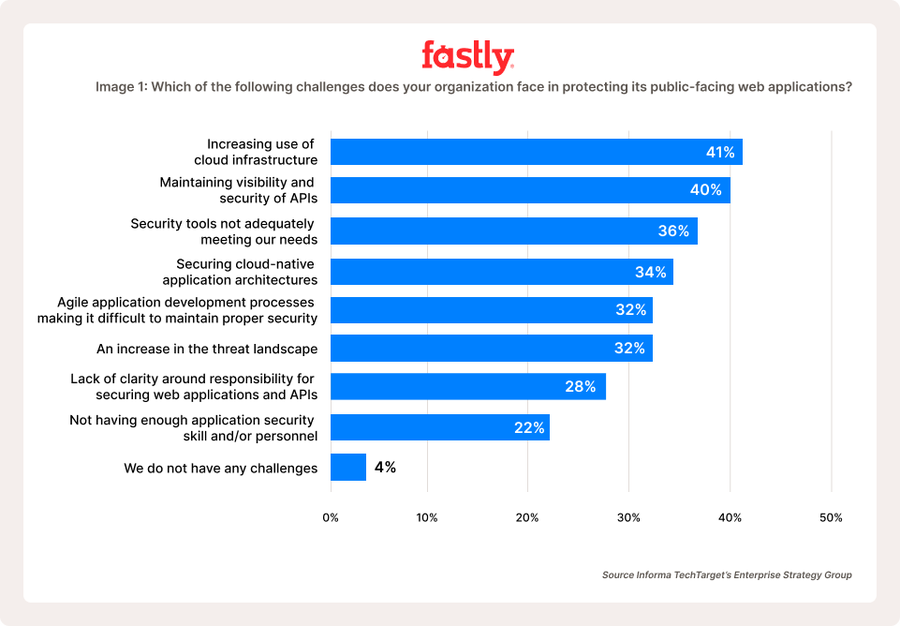
As you relate these stats to your own organization, consider how the adoption of containers, multi-cloud-service-provider configuration, and other infrastructure changes will impact your ability to keep them secure. Can the solutions you have in place today effectively scale with the increased volume of properties and protect everywhere you live? Those polled appear to be unsure that’s the case and thus are exploring how they can consolidate what they’re leveraging.
Consolidation is top of mind
Web application firewalls are synonymous with application security. They’ve been around for decades, and as new PCI 4.0 requirements force organizations to procure one to protect all of their public-facing sites if they haven’t already, the topic of how many the organization really needs is top of mind. PCI requirements aside, WAFs aren’t new to most organizations and 92% of respondents noted their organization has at least one. In fact, 67% of respondents noted that their organization is using multiple from a variety of vendors.
Sound familiar?
When asked why, many of those who noted their increasing use of cloud infrastructure is their biggest challenge also said it’s the reason they’ve been forced to buy multiple WAFs. Some just can’t protect everywhere they need. Other reasons for having multiple WAFs point to requests from application owners and adjacent teams for a specific vendor and unique feature sets some offer (Image 2).

To summarize their responses, it appears that organizations have multiple WAFs for one of two reasons:
They can’t protect everywhere they operate (cloud, on-prem, container, hybrid, etc.)
They aren’t effective enough; and thus, others have been procured to fill perceived gaps.
If your organization is in the same boat, consider these two topics as top criteria in your search; a Next-Gen WAF like Fastly’s may be the consolidated solution you’ve been searching for.
Attackers are launching successful decoys
Putting out attack-related fires is natural and part of the job, but when multiple happen simultaneously, it can push teams beyond what they can stop. Of those who stated they’ve experienced a DDoS attack, 45% noted the DDoS came as a diversion in a broader attack. Of that group, 70% said that the diversion ultimately worked and impacted operations, resulting in data loss, etc. This is a big deal, and in light of this information, consider whether your tabletop exercises and attack simulations include events like these to reduce the likelihood of impacting your organization.
Practice may make perfect, but automation is another method to address these diversions. However, 59% of IT and 55% of cybersecurity roles surveyed believe that AI-powered automation gives adversaries an advantage. While trying Fastly DDoS Protection may tip their disposition in favor of defenders, these stats may also reflect the more scrutinous nature of defenders. Of those surveyed, 56% with developer roles believed cyber-defenders hold the advantage instead (Image 3).
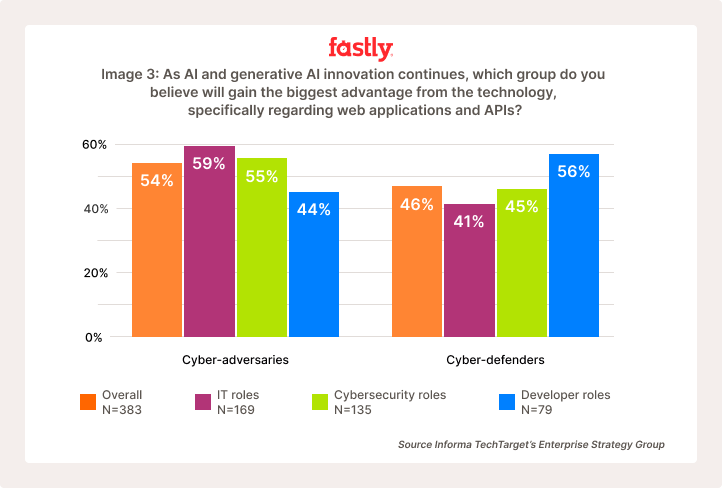
Closing considerations
Applications and the APIs powering them drive massive revenue for organizations, but if they grow at the forecasted rate, we must consider the new opportunities we create for attackers in tandem. Broad security policies across multiple-point solutions may stop attackers despite the opportunities new apps and APIs create, but doing so at the cost of impacting legitimate traffic isn’t an acceptable tradeoff.
Organizations should consider adopting application security solutions that effectively protect environments no matter where they operate or how vast their properties become. As these tools are pulled under one “pane of glass” more teams can shift left and fuel development that security is built into. While we’ve touched on some of the key findings, read the report to dive even deeper into how the industry is shifting. If any of the findings warrant a ticket in your next sprint, contact us to see how we can help.

