Organizations rely on certification authorities (CAs) to sign their digital certificates, establishing trust between users and websites. This ensures that the information transmitted between them is encrypted and secure from eavesdropping and tampering. There are many CAs that organizations can leverage, and Fastly has an integration with three: Let’s Encrypt, GlobalSign, and Certainly (part of Fastly).
Customers who are using Let’s Encrypt should know the changes Let’s Encrypt is making to their chain of trust and how it will affect older devices and operating systems.
What’s changing?
This past July, Let's Encrypt announced, starting on June 6, 2024, that they will stop providing access to their cross-signed chain in preparation for their cross-signed certificate to expire in September 2024. This will shorten its chain of trust by eliminating the cross signature on its immediate certificate.
Let’s Encrypt made the move to reduce operating costs and shift focus to improving customer privacy and security, but the change may impact a percentage of your traffic and prevent them from accessing your site.
What’s happening?
Every browser and operating system maintains a certificate trust store (root certificate store) containing the trusted certificates used to verify the authenticity of SSL or TLS certificates presented by websites and other online services. When new certificate authorities are established, they work with the more established authorities to get a cross-signed signature that validates their own certificates' authenticity.
Picture yourself (a new CA) as not being on the guest list for a party. However, your best friend (an established CA) vouches for you, allowing you to gain entry into the celebration. Similarly, the tenured CA will cross-sign the new CA’s certificates to prove their legitimacy when they aren’t on the trust store’s list of known CAs.
Over time, the new CA will make its way into certificate trust stores as they update, but that is where Let’s Encrypt's dilemma lies. In their early days, they worked with IdenTrust to get a temporary cross-sign of their DST Root Ca X3 certificate while waiting for their own to be widely trusted. Now that they’re trusted in most certificate stores, they’ve opted not to renew this IdenTrust cross-signed certificate.
Their decision impacts older devices and operating systems because their trust stores can’t update. Examples include Android users running less than 7.1.1 and end-users running outdated operating systems or applications that rely on older SSL/TLS libraries.
The impact on end-users
Let’s Encrypt noted in their announcement that the change would cause the trust of approximately 6% of Android devices to be lost. Still, organizations shouldn’t expect their percentage of affected traffic to be identical. For some organizations, the rate could be much higher or lower. While it has been nearly a year since the announcement’s publication, it isn’t clear whether the gap has been closed. Additionally, there is no mention of the other devices and operating systems impacted.
How invalid tokens impact end-users
If an end user’s trust store doesn't contain a valid certificate for the site they’re trying to reach, their browser or operating system will typically display a warning message indicating that the connection is not secure or that the website's certificate is not trusted (Image 1).
Image 1: Invalid token warning
Depending on the severity, they may prevent you from accessing the website altogether or allow them to proceed with caution.
The main business impact of invalid tokens stemming from this change is clear: potential revenue loss, but it doesn’t stop there. The change may also impact the organization’s market reputation and lower their SEO ranking, too.
How Fastly customers can confirm their CA
If you are unsure which CA you are using, log in to the Fastly console and follow these simple steps:
Navigate to the Secure tab
Click on TLS Management
Click on the Subscriptions tab
From this page, you can see the Certification Authority listed in the second column1. If you are using Let’s Encrypt and want to migrate to Certainly, click on the View Subscription Details link, and you will see a Migrate to Certainly link2 (Image 2). Confirm you want to migrate to Certainly, and we will automatically replace your Let’s Encrypt certificate with a Certainly certificate. There will be no downtime, and we will serve your Let’s Encrypt certificate until it is replaced by Certainly.
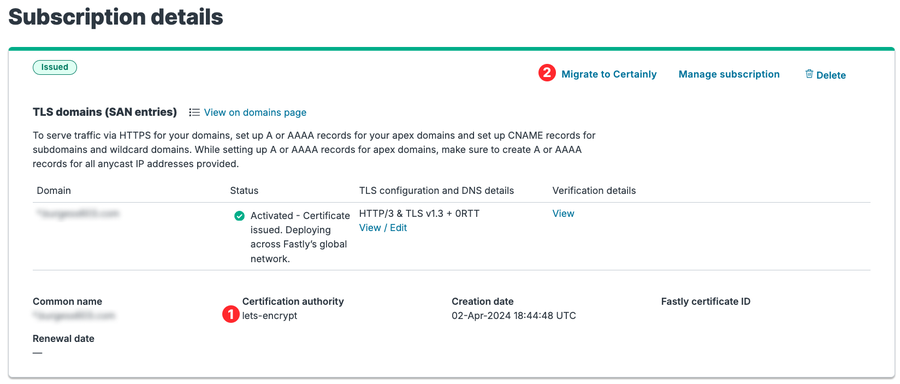
Image 2: Subscription details
How to know whether your traffic is impacted by Let’s Encrypt’s changes
First, determine whether you support devices that do not support up to TLS version 1.2 or higher. If you aren’t, then this change shouldn’t affect your organization. For those supporting these devices, it’s difficult to discern what percentage of traffic will be impacted after June 6. Site operators are encouraged to monitor website usage statistics in Q3 and Q4, as any significant dropoff in Android usage can likely be attributed to the change.
Organizations that can’t take that risk or force customers to adopt a different way of browsing can preemptively switch their certificate authority to Certainly to limit the impact on their customers.
Meet Certainly, Fastly’s Certificate Authority
Certainly is Fastly’s publicly-trusted certification authority. It is available to all Fastly customers and offers three unique benefits:
Tighter security and lower risk at no extra cost with short, 30-day validity periods that reduce the time a compromised certificate is usable.
Simplified, expedited certificate management, even for hundreds of thousands of domains.
More reliable service and better customer support as Fastly is the single point of contact for the entire certificate workflow.
Additionally, Certainly is cross-signed by Starfield to inherit the decades of trust their root CA has accrued. Our commitment to widespread trust allows Certainly to support organizations affected by Let’s Encrypt’s looming changes and beyond. Accepted as a root CA by Mozilla and included in the root stores of Apple and Google, Certainly is a widely accepted CA, and we’re ready to support your organization too. Contact us to learn more!

